Read the original article: New warning issued over COVID‑19 vaccine fraud, cyberattacks Cybercriminals look to cash in on the vaccine rollou...
Read More
Worldwide VPN market to reach $75.59 billion by 2027
Read the original article: Worldwide VPN market to reach $75.59 billion by 2027 The global VPN market was valued at $25.41 Billion in 2019 a...
Read More
2020 set the stage for cybersecurity priorities in 2021
Read the original article: 2020 set the stage for cybersecurity priorities in 2021 It’s safe to assume that pretty much everyone is ready to...
Read More
21 arrested after allegedly using stolen logins to commit fraud
Read the original article: 21 arrested after allegedly using stolen logins to commit fraud UK police also give some food for thought to thos...
Read More

The head of Group-IB Mr. Sachkov described the portrait of a typical Russian hacker
Read the original article: The head of Group-IB Mr. Sachkov described the portrait of a typical Russian hacker Not only a programmer but als...
Read More

A Google Docs Bug Could Have Allowed Hackers See Your Private Documents
Google has patched a bug in its feedback tool incorporated across its services that could be exploited by an attacker to potentially steal s...
Read More
Data security vs data privacy – they’re not the same thing
Read the original article: Data security vs data privacy – they’re not the same thing Data security and data privacy are both necessary to c...
Read More

Freedom Finance’s customer data got leaked after employee fell for phishing attack
Read the original article: Freedom Finance’s customer data got leaked after employee fell for phishing attack Broker Freedom Finance admitte...
Read More
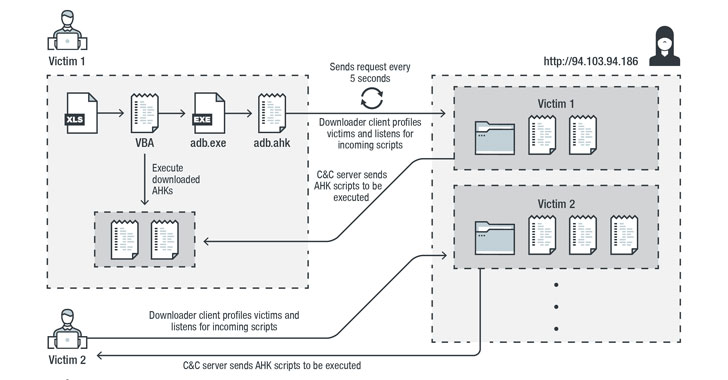
AutoHotkey-Based Password Stealer Targeting US, Canadian Banking Users
Threat actors have been discovered distributing a new credential stealer written in AutoHotkey (AHK) scripting language as part of an ongoin...
Read More
Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 309’
Read the original article: Robert M. Lee’s & Jeff Haas’ Little Bobby Comics – ‘WEEK 309’ via the respected information security capabili...
Read More
DEF CON 28 Safe Mode Demo Labs – Tamoaki Tani’s ‘Malconfscan With Cuckoo’
Read the original article: DEF CON 28 Safe Mode Demo Labs – Tamoaki Tani’s ‘Malconfscan With Cuckoo’ Many thanks to DEF CON and Conference S...
Read More
Phishing Will Continue Wreak Havoc in 2021—Make Sure You’re Ready
Read the original article: Phishing Will Continue Wreak Havoc in 2021—Make Sure You’re Ready The number one cause of a cybersecurity breach ...
Read More
Biggest Security Takeaway of 2020: Don’t Leak Secrets on GitHub
Read the original article: Biggest Security Takeaway of 2020: Don’t Leak Secrets on GitHub 2020 has been crazy, especially in security. We c...
Read More
Leveraging SOC 2 compliance for Cloud (SAAS) services
In a digital world where we often witness high-profile attacks, and incidents of a data breach, considering the implementation of effective ...
Read More

A New SolarWinds Flaw Likely Had Let Hackers Install SUPERNOVA Malware
An authentication bypass vulnerability in the SolarWinds Orion software may have been leveraged by adversaries as zero-day to deploy the SUP...
Read More

10 Different Types of Dangerous Malware Attack and How to Avoid them
Today’s topic is basically about types of malware, yes, it’s a malicious software which is basically designated to damage, impair, or exploi...
Read More

Microsoft Warns CrowdStrike of Hackers Targeting Azure Cloud Customers
New evidence amidst the ongoing probe into the espionage campaign targeting SolarWinds has uncovered an unsuccessful attempt to compromise c...
Read More
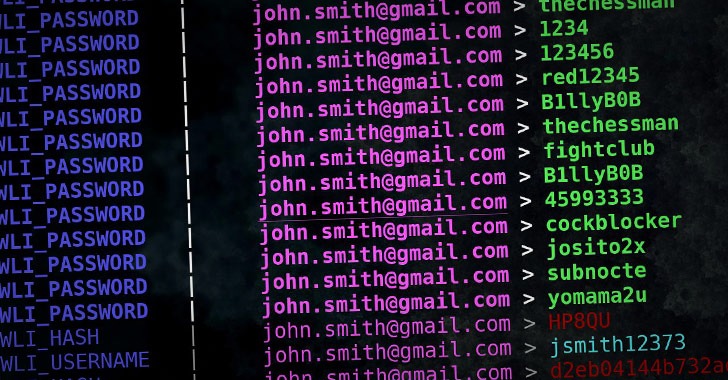
Police Arrest 21 WeLeakInfo Customers Who Bought Breached Personal Data
21 people have been arrested across the UK as part of a nationwide cyber crackdown targeting customers of WeLeakInfo[.]com, a now-defunct on...
Read More
Looking Back on the Year in Apple Security – Intego Mac Podcast Episode 167
Read the original article: Looking Back on the Year in Apple Security – Intego Mac Podcast Episode 167 As the year ends, we look back on the...
Read More
PCI DSS and the Cloud: Top Risk and Mitigation Strategies To Tackle The Challenges
In the digital world, cloud computing is essential for most businesses online. It is a significant technology for your organization, be it o...
Read More

Attackers Abusing Citrix NetScaler Devices to Launch Amplified DDoS Attacks
Citrix has issued an emergency advisory warning its customers of a security issue affecting its NetScaler application delivery controller (A...
Read More
Network operator spend on multi-access edge computing to reach $8.3B by 2025
Read the original article: Network operator spend on multi-access edge computing to reach $8.3B by 2025 Network operator spend on multi-acce...
Read More

Google Discloses Poorly-Patched, Now Unpatched, Windows 0-Day Bug
Google's Project Zero team has made public details of an improperly patched zero-day security vulnerability in Windows print spooler API...
Read More

North Korean Hackers Trying to Steal COVID-19 Vaccine Research
Threat actors such as the notorious Lazarus group are continuing to tap into the ongoing COVID-19 vaccine research to steal sensitive inform...
Read More

Law Enforcement Seizes Joker's Stash — Stolen Credit Card Marketplace
The US Federal Bureau of Investigation (FBI) and Interpol have allegedly seized proxy servers used in connection with Blockchain-based domai...
Read More

New Critical Flaws in Treck TCP/IP Stack Affect Millions of IoT Devices
The US Cybersecurity Infrastructure and Security Agency (CISA) has warned of critical vulnerabilities in a low-level TCP/IP software library...
Read More

Cybercriminals' Favorite Bulletproof VPN Service Shuts Down In Global Action
Law enforcement agencies from the US, Germany, Netherlands, Switzerland, France, along with Europol's European Cybercrime Centre (EC3), ...
Read More

Trukno: “On A Mission To Deliver Cyber Intelligence, Not Cyber News”
Read the original article: Trukno: “On A Mission To Deliver Cyber Intelligence, Not Cyber News” Trukno: Virtual Threat Intelligence Analys...
Read More
Worldwide new account fraud declined 23.2% in 2020
Read the original article: Worldwide new account fraud declined 23.2% in 2020 New account fraud based on ID verification declined 23.2% worl...
Read More

Common Security Misconfigurations and Their Consequences
Everyone makes mistakes. That one sentence was drummed into me in my very first job in tech, and it has held true since then. In the cyberse...
Read More
iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit
Read the original article: iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit Three dozen journalists working for Al Jazeera...
Read More
Five ways COVID-19 will change cybersecurity
Read the original article: Five ways COVID-19 will change cybersecurity The main story of 2021 won’t be the disease, but the vaccine. With t...
Read More

iPhones of 36 Journalists Hacked Using iMessage Zero-Click Exploit
Three dozen journalists working for Al Jazeera had their iPhones stealthily compromised via a zero-click exploit to install spyware as part ...
Read More

Weekly Update 222
Read the original article: Weekly Update 222 Presently sponsored by: 1Password is a secure password manager and digital wallet that keeps yo...
Read More

EFF Calls Facebook’s Criticism of Apple’s Pro-Privacy Tracking Change ‘Laughable’
Read the original article: EFF Calls Facebook’s Criticism of Apple’s Pro-Privacy Tracking Change ‘Laughable’ Facebook’s recent criticism dir...
Read More

IT Security News Daily Summary 2020-12-19
Facebook bug exposed email addresses of Instagram users Trump Downplays Russia in First Comments on Cyberattack DEF CON 28 Safe Mode Hack Th...
Read More

The many ways you can be scammed on Facebook, part II
Read the original article: The many ways you can be scammed on Facebook, part II Read more → The post The many ways you can be scammed o...
Read More

Threat Roundup for December 11 to December 18
Read the original article: Threat Roundup for December 11 to December 18 Today, Talos is publishing a glimpse into the most prevalent threat...
Read More
HPE Patched Critical zero-day in server Management Software
HPE (Hewlett Packard Enterprise) has recently published a critical zero-day bug in one of the latest versions of its exclusive HPE Systems I...
Read More

Microsoft Says Its Systems Were Also Breached in Massive SolarWinds Hack
The massive state-sponsored espionage campaign that compromised software maker SolarWinds also targeted Microsoft, as the unfolding investig...
Read More
Software Supply-Chain Attack Hits Vietnam Government Certification Authority
Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that com...
Read More
How to Use Password Length to Set Best Password Expiration Policy
One of the many features of an Active Directory Password Policy is the maximum password age. Traditional Active Directory environments have ...
Read More

New 5G Network Flaws Let Attackers Track Users' Locations and Steal Data
As 5G networks are being gradually rolled out in major cities across the world, an analysis of its network architecture has revealed a numbe...
Read More
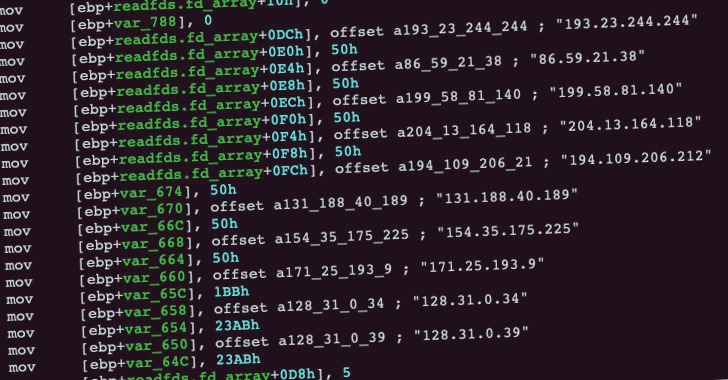
Ransomware Attackers Using SystemBC Malware With RAT and Tor Proxy
Cybercriminals are increasingly outsourcing the task of deploying ransomware to affiliates using commodity malware and attack tools, accordi...
Read More

What is Geocoding? — How to Find Coordinates of An Address
How can your app hook into a geocoding service that offers forward and reverse geocoding and an auto-completion facility? Geocoding turns a ...
Read More

New Goontact spyware discovered targeting Android and iOS users
Read the original article: New Goontact spyware discovered targeting Android and iOS users Most Goontact-laced apps are targeting Asian user...
Read More

45 million medical images left exposed online
Read the original article: 45 million medical images left exposed online More than 45 million medical images – including X-rays and CT scans...
Read More

Accelerated cloud migration may leave business data insecure
Read the original article: Accelerated cloud migration may leave business data insecure The pandemic has accelerated digital transformation ...
Read More

SoReL-20M Sophos & ReversingLabs release 10 million disarmed samples for malware study
Read the original article: SoReL-20M Sophos & ReversingLabs release 10 million disarmed samples for malware study Sophos and ReversingLa...
Read More

Apple addressed multiple code execution flaws in iOS and iPadOS
Read the original article: Apple addressed multiple code execution flaws in iOS and iPadOS Apple addressed this week serious code execution ...
Read More

Secure enclave protection for AI and ML
Read the original article: Secure enclave protection for AI and ML You can’t swing a virtual bat without hitting someone touting the value o...
Read More

How to make DevSecOps stick with developers
Read the original article: How to make DevSecOps stick with developers While DevOps culture has brought innovation to the industry and trans...
Read More

Cyber Attack on US Treasury and Commerce Departments
Read the original article: Cyber Attack on US Treasury and Commerce Departments The FBI and the Department of Homeland Security have issued ...
Read More

US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor
State-sponsored actors allegedly working for Russia have targeted the US Treasury, the Commerce Department's National Telecommunications...
Read More

DEF CON 28 Safe Mode Aerospace Village – Panel: ‘Building Connections Across The Aviation Ecosystem’
Read the original article: DEF CON 28 Safe Mode Aerospace Village – Panel: ‘Building Connections Across The Aviation Ecosystem’ Many thanks ...
Read More
Amnesia:33 – 33 Vulnerabilities That Impact Four Open-source TCP/IP Stacks Affects Millions of IoT Devices
The cybersecurity researchers have been warning regarding a set of very severe vulnerabilities that are continuously affecting TCP/IP stacks...
Read More

What is the Different Between VPN and Proxy – A Complete Guide
Both the VPN and proxy are used to facilitate the connection between the client and server by hiding it’s IP address and they are slightly d...
Read More
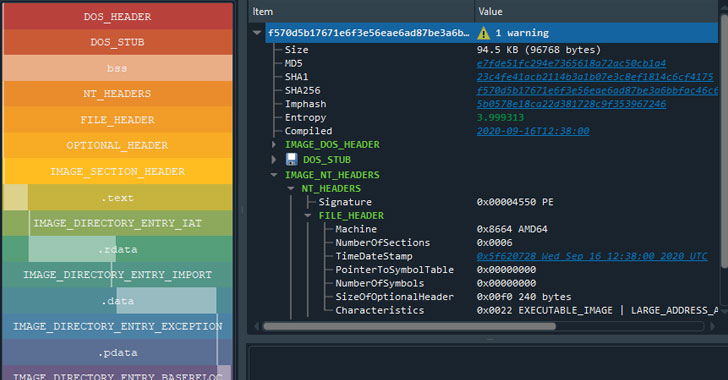
Mount Locker Ransomware Offering Double Extortion Scheme to Other Hackers
A relatively new ransomware strain behind a series of breaches on corporate networks has developed new capabilities that allow it to broaden...
Read More

Watch Out! Adrozek Malware Hijacking Chrome, Firefox, Edge, Yandex Browsers
Microsoft on Thursday took the wraps off an ongoing campaign impacting popular web browsers that stealthily injects malware-infested ads int...
Read More

Governance Considerations for Democratizing Your Organization's Data in 2021
With the continuing rise of IoT devices, mobile networks, and digital channels, companies face a lot of pressure to generate meaningful and ...
Read More

Facebook Tracks APT32 OceanLotus Hackers to IT Company in Vietnam
Cybersecurity researchers from Facebook today formally linked the activities of a Vietnamese threat actor to an IT company in the country af...
Read More
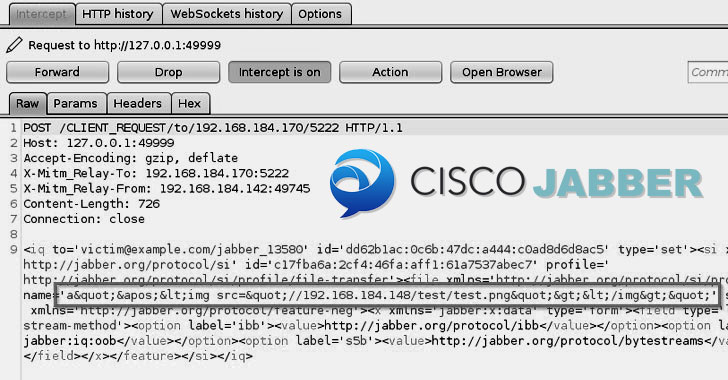
Cisco Reissues Patches for Critical Bugs in Jabber Video Conferencing Software
Cisco has once again fixed four previously disclosed critical bugs in its Jabber video conferencing and messaging app that were inadequately...
Read More

Valve's Steam Server Bugs Could've Let Hackers Hijack Online Games
Critical flaws in a core networking library powering Valve's online gaming functionality could have allowed malicious actors to remotely...
Read More

48 U.S. States and FTC are suing Facebook for illegal monopolization
The US Federal Trade Commission and a coalition of 48 state attorneys general on Wednesday filed a pair of sweeping antitrust suits against ...
Read More
Subscribe to:
Comments (Atom)