ProxyToken, a serious security vulnerability has been detected in the Microsoft Exchange Server by the security analysts. ProxyToken vulnera...
Read More

New Microsoft Exchange 'ProxyToken' Flaw Lets Attackers Reconfigure Mailboxes
Details have emerged about a now-patched security vulnerability impacting Microsoft Exchange Server that could be weaponized by an unauthent...
Read More

Fujitsu says stolen data being sold on dark web ‘related to customers’
This article has been indexed from Latest topics for ZDNet in Security A group called “Marketo” has claimed it has 4 GB of stolen data and p...
Read More
New Vulnerability Allow Hackers to Bypass PIN Codes on Contactless Cards From Mastercard & Maestro
The cybersecurity researchers at the Swiss Higher Technical School of Zurich have recently identified a critical vulnerability that allows a...
Read More

Boston Public Library hit by Cyber Attack
This article has been indexed from Cybersecurity Insiders Boston Public Library (BPL) branches based in Massachusetts have been witnessing a...
Read More

T-Mobile hacker used brute force attack to steal customers’ data
This article has been indexed from HackRead By Saad Rajpoot A 21-year-old US citizen named John Binns has claimed responsibility for the T-M...
Read More

Universal Control Works in macOS Monterey Beta 5, But Terminal Commands Required to Enable It
This article has been indexed from MacRumors: Mac News and Rumors – Front Page One of the most highly anticipated features coming to macOS M...
Read More

Get Lifetime Access to 24 Professional Cybersecurity Certification Prep Courses
Not all heroes wear capes. Cybersecurity professionals are digital warriors who use their knowledge and skill to battle malicious hackers. ...
Read More

Five iPhone 13 Rumors You May Have Missed
This article has been indexed from MacRumors: Mac News and Rumors – Front Page We’re just weeks away from when Apple will announce the iPhon...
Read More

Multiple Vulnerabilities Spotted In elFinder File Manager WordPress Plugin
This article has been indexed from Latest Hacking News Numerous critical security vulnerabilities riddled the file manager plugin elFinder. ...
Read More

Apache Kafka as Real-Time Backbone for Cybersecurity
This article has been indexed from DZone Security Zone Apache Kafka became the de facto standard for processing data in motion across enterp...
Read More

Cloudflare says it stopped the largest DDoS attack ever reported
This article has been indexed from Latest topics for ZDNet in Security Cloudflare’s system detected and mitigated a 17.2 million request-per...
Read More
IoT Botnet Attack Hundreds of Thousands of Realtek Chipset Based Devices
The IoT security firm, SAM has recently discovered a dangerous botnet attacking devices using the Realtek chipsets. Not only this even this...
Read More
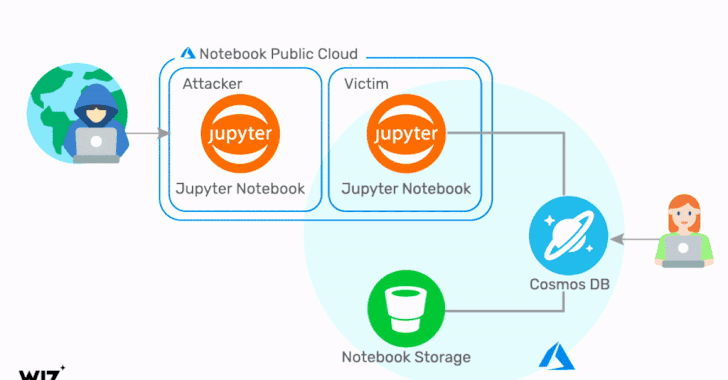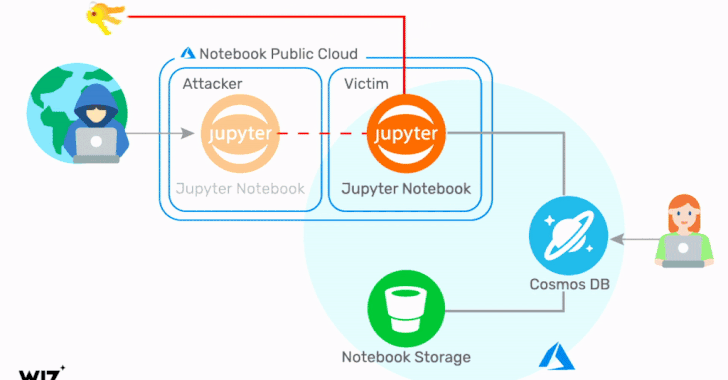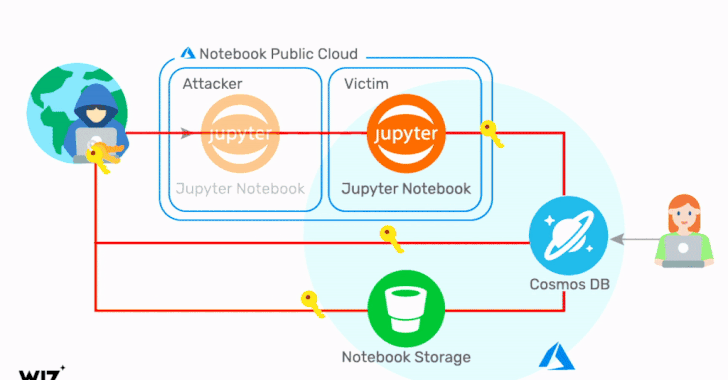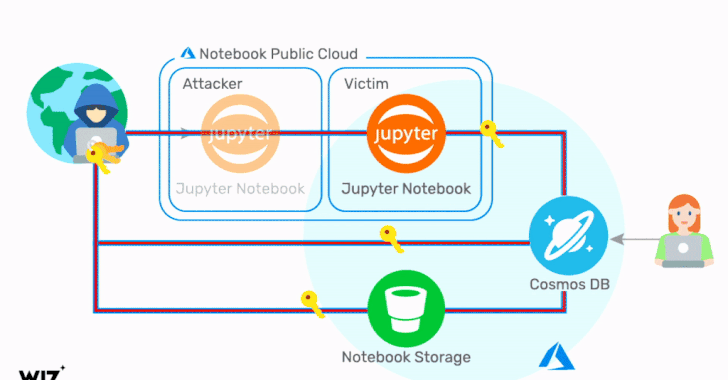
Critical Cosmos Database Flaw Affected Thousands of Microsoft Azure Customers
Cloud infrastructure security company Wiz on Thursday revealed details of a now-fixed Azure Cosmos database vulnerability that could have be...
Read More
APT Hackers Attack Retails Firms in U.S Using SideWalk Backdoor
The security researchers of the antivirus company ESET have recently detected the SideWalk modular backdoor, this backdoor has been used by ...
Read More
New Passwordless Verification API Uses SIM Security for Zero Trust Remote Access
Forget watercooler conspiracies or boardroom battles. There's a new war in the office. As companies nudge their staff to return to commu...
Read More

Critical Flaw Discovered in Cisco APIC for Switches — Patch Released
Cisco Systems on Wednesday issued patches to address a critical security vulnerability affecting the Application Policy Infrastructure Contr...
Read More
Beware!! New Modified Version of WhatsApp Install Malware on Your Device & Steal SMS Data
The Kaspersky Lab has recently discovered the Trojan Triada, in one of the versions of the mod for the WhatsApp messenger – FMWhatsapp16.80....
Read More
4 New Emerging Ransomware Groups That Can a Serious Threat To Enterprises And Critical Infrastructure
Palo Alto Networks’ Unit 42 threat intelligence team observed four emerging ransomware groups that are currently affecting organizations and...
Read More

New SideWalk Backdoor Targets U.S.-based Computer Retail Business
A computer retail company based in the U.S. was the target of a previously undiscovered implant called SideWalk as part of a recent campaign...
Read More

Samsung delivers PIM technology to a wider range of applications
This article has been indexed from Help Net Security Samsung showcased its latest advancements with processing-in-memory (PIM) technology at...
Read More
Protect Your Enterprise From ShinyHunters APT Hackers Group That Responsible for Notable Cyber Attacks
The security researchers of Intel 471 have recently detected a cybercriminal group ShinyHunters that is continuously trying to collect all e...
Read More

Google bans the following cryptocurrency apps for data security
This article has been indexed from Cybersecurity Insiders If you are a cryptocurrency enthusiast and are using any of the mining apps to ear...
Read More

Microsoft Spills 38 Million Sensitive Data Records Via Careless Power App Configs
This article has been indexed from Threatpost Data leaked includes COVID-19 vaccination records, social security numbers and email addresses...
Read More
Warning! Attackers Compromise Over 2000 Microsoft Exchange Servers With ProxyShell Flaws
Over the past two days, the hackers have compromised almost 2000 Microsoft Exchange servers and installed backdoors on those hacked 2000 Mic...
Read More
Top 10 Kubernetes Container Scanner to Detect Security Vulnerability and Misconfiguration
Before you read this topic, you may be wondering what Kubernetes is? Let us tell you; it is an extensible, portable, and open-source platfor...
Read More

Four Ways Smart Cities Can Stay Safe in An Interconnected World
This article has been indexed from Cyber Defense Magazine Mitigating the risks of cyber threats through cyber intelligence and frontier tech...
Read More
WARNING: Microsoft Exchange Under Attack With ProxyShell Flaws
The U.S. Cybersecurity and Infrastructure Security Agency is warning of active exploitation attempts that leverage the latest line of "...
Read More

Most Important Web Server Penetration Testing Checklist
This article has been indexed from GBHackers On Security Web server pentesting performing under 3 major category which is identity, Analyse,...
Read More

New LockFile ransomware gang uses ProxyShell and PetitPotam exploits
This article has been indexed from Security Affairs A new ransomware gang named LockFile targets Microsoft Exchange servers exploiting the r...
Read More
Largest HTTP DDoS Attack That Peaking At 17.2 Million Requests Per Second
Cloudflare stated that it mitigated a 17.2 million request-per-second (rps) DDoS attack, an attack about three times larger than any previou...
Read More

NYC Teachers’ Social Security Numbers Exposed
This article has been indexed from http://www.infosecurity-magazine.com/rss/news/76/application-security/ Data breach reported by students w...
Read More

Emsisoft releases free SynAck ransomware decryptor
This article has been indexed from Security Affairs Emsisoft researchers have released a decryptor for the SynAck Ransomware that could allo...
Read More
North Korean APT Hackers Attack Victims Using MS IE & Edge Browser Exploits
Researchers uncovered a new browser-based attackers from the infamous North Korean APT Hackers groups targeting the victims with the differe...
Read More
Critical Flaw Found in Older Cisco Small Business Routers Won't Be Fixed
A critical vulnerability in Cisco Small Business Routers will not be patched by the networking equipment giant, since the devices reached en...
Read More
Hackers Breached US Census Bureau in 2020 Using Citrix Exploit
According to the report published by the US Office of Inspector General (OIG), on January 11, 2020, the servers operated by the US Census Bu...
Read More
New HolesWarm Botnet Exploiting 20 Known Vulnerabilities To Attack Windows & Linux Servers
The cybersecurity researchers at Tencent Cloud Firewall have recently detected a new highly volatile botnet which is dubbed as HolesWarm. T...
Read More
How Hackers Break Two-Factor Authentication Security By Intercepting SMS and Voice Calls
The latest findings state that more than 80% of all hacking-related breaches happen due to compromised and weak credentials, with three bi...
Read More
What are Residential Proxies? – Pros & Cons
Proxy is an intermediate server of the Internet connection between the user and an Internet website. Such a connection scheme helps avoid th...
Read More

Does a VPN Protect You from Hackers?
A virtual private network (VPN) is the perfect solution for a lot of issues you might experience online- accessing blocked sites, hiding you...
Read More
STARTTLS Flaws in Email Clients Let Hackers Steak The Credentials From Apple Mail, Gmail, Mozilla Thunderbird
Nearly 40 different vulnerabilities were exposed lately by security researchers that are correlated with an opportunistic encryption mechani...
Read More

Alert: Fraudsters Stealing Bank Account Details via Fake Facebook Pages
This article has been indexed from CYREN Blog RSS Feed I recently received an SMS notification from my bank about possible fraudulent activi...
Read More
Hackers Claimed To Steal Data of 100 Million T-Mobile Customers – Server Hack Confirmed
T-Mobile suffered a data breach that contains the personal details of more than 100 million customers. In an announcement published Monday, ...
Read More

Multiple Flaws Affecting Realtek Wi-Fi SDKs Impact Nearly a Million IoT Devices
Taiwanese chip designer Realtek is warning of four security vulnerabilities in three software development kits (SDKs) accompanying its WiFi ...
Read More
Top 10 Best Open Source Intelligence Tools (OSINT Tools) for Penetration Testing 2021
We all know very well that getting or gathering any information by using various tools become really easy. In this article, we have discusse...
Read More

Dozens of STARTTLS Related Flaws Found Affecting Popular Email Clients
Security researchers have disclosed as many as 40 different vulnerabilities associated with an opportunistic encryption mechanism in mail cl...
Read More
New AdLoad Variant Bypasses Apple's Security Defenses to Target macOS Systems
A new wave of attacks involving a notorious macOS adware family has evolved to leverage around 150 unique samples in the wild in 2021 alone,...
Read More

This Week in Security News – August 13, 2021
This article has been indexed from Trend Micro Simply Security This Week in Security News: Hackers Steal $600 million in Largest Ever Crypto...
Read More
Facebook Added an End-to-End Encrypted for Messengers Audio & Video Call
Nowadays the communication over digital mediums are becoming more common, whether it’s for work, personal, or education. And that’s why the ...
Read More
Ransomware Operators Exploiting Windows Print Spooler Vulnerabilities
The cybersecurity researchers at Cisco Talos have detected that the ransomware group the Vice Society actively exploiting the PrintNightmare...
Read More
Subscribe to:
Posts (Atom)