Read the original article: Wireshark 3.4.3 Released, (Sun, Jan 31st) Wireshark version 3.4.3 was released. Become a supporter of IT Securi...
Read More
USCellular Hacked – Hackers Gained access to its CRM Software
USCellular is one of the mobile network operators that protect its customer’s privacy and strictly follows all its protection policies. But,...
Read More
UScellular data breach: attackers ported customer phone numbers
Read the original article: UScellular data breach: attackers ported customer phone numbers US wireless carrier UScellular discloses data bre...
Read More
Parler Whack-a-Mole
Read the original article: Parler Whack-a-Mole (this is an unrolled Twitter thread converted to the blog since one never knows how long cont...
Read More

Apple Extends Monthly Credit Deposits to Apple TV+ Subscribers Through June
Read the original article: Apple Extends Monthly Credit Deposits to Apple TV+ Subscribers Through June Apple TV+ subscribers have begun rece...
Read More

Google uncovers new iOS security feature Apple quietly added after zero-day attacks
Google Project Zero on Thursday disclosed details of a new security mechanism that Apple quietly added to iOS 14 as a countermeasure to prev...
Read More
New CISOs Survey Reveals How Small Cybersecurity Teams Can Confront 2021
Read the original article: New CISOs Survey Reveals How Small Cybersecurity Teams Can Confront 2021 The pressure on small to medium-sized en...
Read More

New CISOs Survey Reveals How Small Cybersecurity Teams Can Confront 2021
The pressure on small to medium-sized enterprises to protect their organizations against cyberthreats is astronomical. These businesses face...
Read More

Italy CERT Warns of a New Credential Stealing Android Malware
Researchers have disclosed a new family of Android malware that abuses accessibility services in the device to hijack user credentials and r...
Read More
Emotet Takedown – What’s Next
Read the original article: Emotet Takedown – What’s Next A global takedown operation has disrupted Emotet, a prolific form of malware active...
Read More
Apple: New App Tracking Transparency
Read the original article: Apple: New App Tracking Transparency Apple has announced it will introduce a new privacy control feature in the s...
Read More

Warning Issued Over Hackable ADT's LifeShield Home Security Cameras
Newly discovered security vulnerabilities in ADT's Blue (formerly LifeShield) home security cameras could have been exploited to hijack ...
Read More
Best Laptops for Engineering Students 2021
Read the original article: Best Laptops for Engineering Students 2021 There are many types of laptops on the market today. Technology is dev...
Read More
7 Best SoundBars in India Under 10000 Rupees 2021
Read the original article: 7 Best SoundBars in India Under 10000 Rupees 2021 Buying soundbars is always a great option, because of speakers ...
Read More
Tesla Filed a Lawsuit Against Former Employee for Allegedly Stealing Software Code
Recently, the American electric vehicle company Tesla has prosecuted one of its retired employees; Telsa claimed that this employee was alle...
Read More
Cigarette smugglers’ activities up in smoke after illegal factories dismantled across Europe
Read the original article: Cigarette smugglers’ activities up in smoke after illegal factories dismantled across Europe On 21 January, close...
Read More
Critical Vulns Discovered in Vendor Implementations of Key OT Protocol
Read the original article: Critical Vulns Discovered in Vendor Implementations of Key OT Protocol Flaws allow denial-of-service attacks and ...
Read More
N. Korean Hackers Targeting Security Experts to Steal Undisclosed Researches
Google on Monday disclosed details about an ongoing campaign carried out by a government-backed threat actor from North Korea that has targe...
Read More

Beware — A New Wormable Android Malware Spreading Through WhatsApp
A newly discovered Android malware has been found to propagate itself through WhatsApp messages to other contacts in order to expand what ap...
Read More
Pen Testing By Numbers: Tracking Pen Testing Trends and Challenges
Over the years, penetration testing has had to change and adapt alongside the IT environments and technology that need to be assessed. Broad...
Read More
How to Protect Your IoT Devices From Botnet Attacks
IoT devices allow us to connect everything and make our environment smart. However, the technology has always been marred by insecurity, wit...
Read More
Flash Is Dead—but Not Gone
Read the original article: Flash Is Dead—but Not Gone Zombie versions of Adobe’s troubled software can still cause problems in systems aroun...
Read More

Data Breach: Chipmaker Intel Shares Fall by 9%
Read the original article: Data Breach: Chipmaker Intel Shares Fall by 9% The stock of Intel Corp was rallied to close in the last minutes...
Read More

Apple Elaborates on Potential for iPhone 12 and MagSafe Accessories to Interfere With Implantable Medical Devices
Read the original article: Apple Elaborates on Potential for iPhone 12 and MagSafe Accessories to Interfere With Implantable Medical Devices...
Read More
CyberChef: Analyzing OOXML Files for URLs, (Sat, Jan 23rd)
Read the original article: CyberChef: Analyzing OOXML Files for URLs, (Sat, Jan 23rd) In diary entry “Doc & RTF Malicious Document” I st...
Read More

Experts Detail A Recent Remotely Exploitable Windows Vulnerability
More details have emerged about a security feature bypass vulnerability in Windows NT LAN Manager (NTLM) that was addressed by Microsoft as ...
Read More

Exclusive: SonicWall Hacked Using 0-Day Bugs In Its Own VPN Product
SonicWall, a popular internet security provider of firewall and VPN products, on late Friday disclosed that it fell victim to a coordinated ...
Read More
Impacts of Website Security on SEO Rankings and How to Manage Them
Read the original article: Impacts of Website Security on SEO Rankings and How to Manage Them Did you know that your website security or its...
Read More
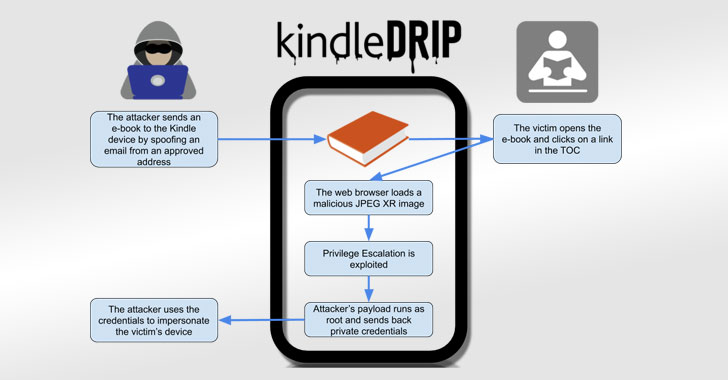
Sharing eBook With Your Kindle Could Have Let Hackers Hijack Your Account
Amazon has addressed a number of flaws in its Kindle e-reader platform that could have allowed an attacker to take control of victims' d...
Read More
DNSpooq Vulnerability In DNS software Let Attackers hijack Millions of Network Devices
Recently, cybersecurity experts have detected nearly 7 vulnerabilities in a very popular DNS software set that has been executed in routers ...
Read More
Hackers Accidentally Expose Passwords Stolen From Businesses On the Internet
A new large-scale phishing campaign targeting global organizations has been found to bypass Microsoft Office 365 Advanced Threat Protection ...
Read More

Importance of Application Security and Customer Data Protection to a Startup
When you are a startup, there are umpteen things that demand your attention. You must give your hundred percent (probably even more!) to wor...
Read More
Bugs in Facebook, Google chat, JioChat Let Attackers Spy on the Users
Google’s Project Zero security researcher, Natalie Silvanovich discovered a serious vulnerability in Group FaceTime which allowed an attacke...
Read More

Apple Said to Be Driving Market Growth of Ultra Wideband Applications
Read the original article: Apple Said to Be Driving Market Growth of Ultra Wideband Applications Apple’s inclusion of Ultra Wideband chips i...
Read More

Google Discloses Flaws in Signal, FB Messenger, JioChat Messaging Apps
In January 2019, a critical flaw was reported in Apple's FaceTime group chats feature that made it possible for users to initiate a Face...
Read More

Researchers Discover Raindrop — 4th Malware Linked to the SolarWinds Attack
Cybersecurity researchers have unearthed a fourth new malware strain—designed to spread the malware onto other computers in victims' net...
Read More

New Educational Video Series for CISOs with Small Security Teams
Cybersecurity is hard. For a CISO that faces the cyber threat landscape with a small security team, the challenge is compounded. Compared to...
Read More
FreakOut! Ongoing Botnet Attack Exploiting Recent Linux Vulnerabilities
An ongoing malware campaign has been found exploiting recently disclosed vulnerabilities in Linux devices to co-opt the systems into an IRC ...
Read More
Application security testing is not just buzzwords
If you develop software, especially security software, and you don’t do this type of tests, then you might endanger your customers, you migh...
Read More
Rob Joyce Appointed Director of Cybersecurity at NSA
Read the original article: Rob Joyce Appointed Director of Cybersecurity at NSA The U.S. National Security Agency on Friday announced that R...
Read More
MoD Experiences 18% Growth in Personal Data Loss Incidents
Read the original article: MoD Experiences 18% Growth in Personal Data Loss Incidents MoD saw incidents rise by 18% year-on-year Become a ...
Read More

Apple Removes macOS Feature That Allowed Apps to Bypass Firewall Security
Apple has removed a controversial feature from its macOS operating system that allowed the company's own first-party apps to bypass cont...
Read More
Security Affairs newsletter Round 297
Read the original article: Security Affairs newsletter Round 297 A new round of the weekly SecurityAffairs newsletter arrived! Every week th...
Read More
Week in review: Pen testing, Sunspot malware, Microsoft plugs Defender zero-day
Read the original article: Week in review: Pen testing, Sunspot malware, Microsoft plugs Defender zero-day Here’s an overview of some of las...
Read More
Authorities Take Down the Worlds Largest Illegal Dark web Market Place
DarkMarket is one of the world’s largest illegal market on the web, and recently, this market has been shut down by many countries like Germ...
Read More
Big Tech Can’t Ban Its Way Out of This
Read the original article: Big Tech Can’t Ban Its Way Out of This Platforms are scrambling to avoid being used by right-wing extremists targ...
Read More

WhatsApp Delays Controversial 'Data-Sharing' Privacy Policy Update By 3 Months
WhatsApp said on Friday that it wouldn't enforce its recently announced controversial data sharing policy update until May 15. Originall...
Read More

Joker's Stash, The Largest Carding Marketplace, Announces Shutdown
Joker's Stash, the largest dark web marketplace notorious for selling compromised payment card data, has announced plans to shut down it...
Read More
Australian Government Slams Google For Blocking Local Content
Read the original article: Australian Government Slams Google For Blocking Local Content Users in Australia complain after Google blocks loc...
Read More

Researchers Disclose Undocumented Chinese Malware Used in Recent Attacks
Cybersecurity researchers have disclosed a series of attacks by a threat actor of Chinese origin that has targeted organizations in Russia a...
Read More
New Malware That Uses WiFi BSSID to Determine the Victim’s Location
The cybersecurity researchers at SANS Internet Storm Center’s Xavier Mertens recently recognized malware that utilizes an exciting method to...
Read More
Hackers bypassed the US Cybersecurity Agency’s MFA
Read the original article: Hackers bypassed the US Cybersecurity Agency’s MFA Today the US Cybersecurity and Infrastructure Security Agency ...
Read More
Entrust acquires HyTrust to offer identity, encryption and security policy control for cloud environments
Read the original article: Entrust acquires HyTrust to offer identity, encryption and security policy control for cloud environments Entrust...
Read More

Intel Adds Hardware-Enabled Ransomware Detection to 11th Gen vPro Chips
Intel and Cybereason have partnered to build anti-ransomware defenses into the chipmaker's newly announced 11th generation Core vPro bus...
Read More
Ubiquiti Urges Customers To Quickly Enable 2FA
Read the original article: Ubiquiti Urges Customers To Quickly Enable 2FA It has been reported that Ubiquiti, a major vendor of cloud-enable...
Read More
Protecting The Digitally-excluded: Biometric Identification Ensures Access To Payments In A Cashless World
Read the original article: Protecting The Digitally-excluded: Biometric Identification Ensures Access To Payments In A Cashless World The ev...
Read More

Warning — 5 New Trojanized Android Apps Spying On Users In Pakistan
Cybersecurity researchers took the wraps off a new spyware operation targeting users in Pakistan that leverages trojanized versions of legit...
Read More
Unveiled: SUNSPOT Malware Was Used to Inject SolarWinds Backdoor
As the investigation into the SolarWinds supply-chain attack continues, cybersecurity researchers have disclosed a third malware strain that...
Read More

Researchers Find Links Between Sunburst and Russian Kazuar Malware
Cybersecurity researchers, for the first time, may have found a potential connection between the backdoor used in the SolarWinds hack to a p...
Read More
Juspay Hacked – Over 100 Million Users Data Leaked in Dark web
The cybersecurity researchers have recently detected a data breach of Juspay’s servers. And according to the experts’ report, in this data b...
Read More
Two market analysts flag their favorite high-flying trades with stocks at records
Read the original article: Two market analysts flag their favorite high-flying trades with stocks at records Two traders share their best tr...
Read More
SolarWinds takes a leaf out of Zoom’s book, hires A-Team of Stamos and Krebs to sort out its security woes
Read the original article: SolarWinds takes a leaf out of Zoom’s book, hires A-Team of Stamos and Krebs to sort out its security woes The we...
Read More
Dassault Falcon Jet Disclosed Data Breach – Ransomware Attack Suspected
Read the original article: Dassault Falcon Jet Disclosed Data Breach – Ransomware Attack Suspected Another sensitive corporation has suffere...
Read More
Glofox – 2,330,735 breached accounts
Read the original article: Glofox – 2,330,735 breached accounts In March 2020, the Irish gym management software company Glofox suffered a d...
Read More

Apple Suspends Parler From App Store After Failing to Take ‘Adequate Measures’ to Address Dangerous Content
Read the original article: Apple Suspends Parler From App Store After Failing to Take ‘Adequate Measures’ to Address Dangerous Content Apple...
Read More
Streaming Wars as a Hotbed for Cybercriminals: Scope and Attacks
Time and again, Cybercriminals have forayed into the digital space, mostly convoyed with newer strategies to breach, attack, and plunder us ...
Read More

Russian hackers selling program in darknet that bypasses spam protection
Read the original article: Russian hackers selling program in darknet that bypasses spam protection The Russian-language Darknet site sells ...
Read More
Intellyx Predictions for 2021: Cyberwar, Crypto Crash, and COVID End
Read the original article: Intellyx Predictions for 2021: Cyberwar, Crypto Crash, and COVID End Welcome to our eighteenth annual installment...
Read More

New Attack Could Let Hackers Clone Your Google Titan 2FA Security Keys
Hardware security keys—such as those from Google and Yubico—are considered the most secure means to protect accounts from phishing and takeo...
Read More
Want your endpoint security product in the ‘Microsoft Consumer Antivirus Providers for Windows’ ?
You need to meet some serious performance and functionality requirements. Don’t try to do this yourself because you will need a long time an...
Read More
ALERT: North Korean hackers targeting South Korea with RokRat Trojan
A North Korean hacking group has been found deploying the RokRat Trojan in a new spear-phishing campaign targeting the South Korean governme...
Read More

How Does Your AD Password Policy Compare to NIST's Password Recommendations?
End-user passwords are one of the weakest components of your overall security protocols. Most users tend to reuse passwords across work and ...
Read More
FBI Warn Hackers are Using Hijacked Home Security Devices
The U.S. Federal Bureau of Investigation has recently reported that the threat actors are hacking home security systems and applying them to...
Read More

SolarWinds Hackers Also Accessed U.S. Justice Department's Email Server
The U.S. Department of Justice on Wednesday became the latest government agency in the country to admit its internal network was compromised...
Read More

Hackers Using Fake Trump's Scandal Video to Spread QNode Malware
Cybesecurity researchers today revealed a new malspam campaign that distributes a remote access Trojan (RAT) by purporting to contain a sex ...
Read More
Google Speech-to-Text API Can Help Attackers Easily Bypass Google reCAPTCHA
A three-year-old attack technique to bypass Google's audio reCAPTCHA by using its own Speech-to-Text API has been found to still work wi...
Read More

Warning: Cross-Platform ElectroRAT Malware Targeting Cryptocurrency Users
Cybersecurity researchers today revealed a wide-ranging scam targeting cryptocurrency users that began as early as January last year to dist...
Read More

Healthcare Industry Witnessed 45% Spike in Cyber Attacks Since Nov 20
Cyberattacks targeting healthcare organizations have spiked by 45% since November 2020 as COVID-19 cases continue to increase globally. Acco...
Read More

British Court Rejects U.S. Request to Extradite WikiLeaks' Julian Assange
A British court has rejected the U.S. government's request to extradite Wikileaks founder Julian Assange to the country on charges perta...
Read More
NCA Arrested 21 Customers who Advertised Stolen Personal Credentials
Britain’s National Crime Agency announced that 21 individuals have been arrested across the UK on suspicion of purchasing personally identif...
Read More
Subscribe to:
Comments (Atom)