Recently, security researchers have found an android malware, and it has been dubbed as Vulture that is a Remote Access Trojan (RAT). Accord...
Read More

This ethical hacking course could give your cybersecurity career a boost
This article has been indexed from Security on TechRepublic Move up in the profitable field of cybersecurity by improving your ethical hacki...
Read More
Beware!! Phone Call Centers Trick Windows Users to Install Malware For Data Exfiltration & Credential Theft
Security researchers from Microsoft observed a new tricks users by attackers to download the BazaLoader malware on windows Users computers t...
Read More
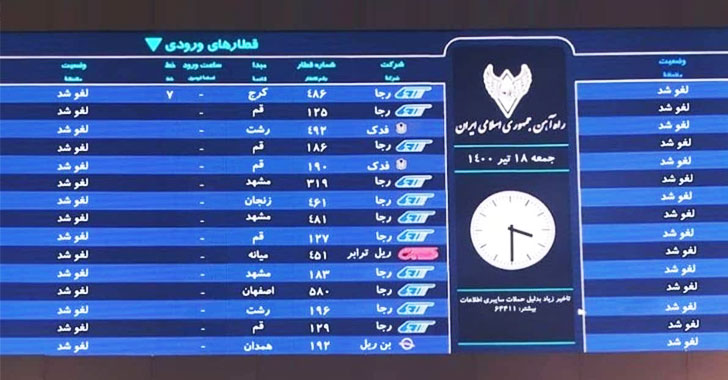
A New Wiper Malware Was Behind Recent Cyberattack On Iranian Train System
A cyber attack that derailed websites of Iran's transport ministry and its national railway system earlier this month, causing widesprea...
Read More

Inmarsat ORCHESTRA integrates GEO, LEO and terrestrial 5G into one solution
This article has been indexed from Help Net Security Inmarsat unveiled plans for ORCHESTRA, the communications network of the future. In the...
Read More

Hackers Exploit Microsoft Browser Bug to Deploy VBA Malware on Targeted PCs
An unidentified threat actor has been exploiting a now-patched zero-day flaw in Internet Explorer browser to deliver a fully-featured VBA-ba...
Read More

Top 30 Critical Security Vulnerabilities Most Exploited by Hackers
Intelligence agencies in Australia, the U.K., and the U.S. issued a joint advisory on Wednesday detailing the most exploited vulnerabilities...
Read More

Most Twitter users haven’t enabled 2FA yet, report reveals
This article has been indexed from WeLiveSecurity Twitter’s transparency report revealed that users aren’t quick to adopt 2FA and once they ...
Read More

UBEL is the New Oscorp — Android Credential Stealing Malware Active in the Wild
An Android malware that was observed abusing accessibility services in the device to hijack user credentials from European banking applicati...
Read More

Biden: Major cyber attack could lead to a ‘real shooting war’
This article has been indexed from Latest topics for ZDNet in Security Joe Biden sends a warning that ‘a cyber breach of great consequence’ ...
Read More

EMQ X Cloud now available on Microsoft Azure to help users carry out their IoT projects with MQTT
This article has been indexed from Help Net Security EMQ announced that EMQ X Cloud is now available on Microsoft Azure. EMQ X Cloud is a fu...
Read More

Apple Releases Urgent 0-Day Bug Patch for Mac, iPhone and iPad Devices
Apple on Monday rolled out an urgent security update for iOS, iPadOS, and macOS to address a zero-day flaw that it said may have been active...
Read More
What is Kerberos Authentication, How it Works, and its Advantages?
Kerberos authentication is a cryptography-based protocol that is used to secure logins. The Kerberos is a mythological three-headed Greek cr...
Read More

Blue Hexagon integrates with AWS Network Firewall to offer protection against unknown cloud threats
This article has been indexed from Help Net Security Blue Hexagon announced the native integration of Blue Hexagon’s real-time deep learning...
Read More
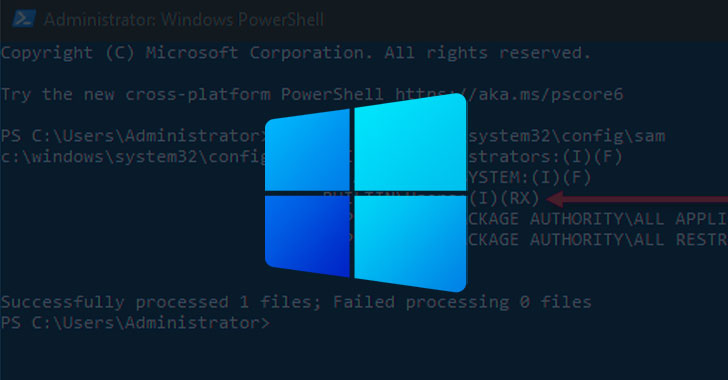
How to Mitigate Microsoft Windows 10, 11 SeriousSAM Vulnerability
Microsoft Windows 10 and Windows 11 users are at risk of a new unpatched vulnerability that was recently disclosed publicly. As we reported ...
Read More

New PetitPotam NTLM Relay Attack Lets Hackers Take Over Windows Domains
A newly uncovered security flaw in the Windows operating system can be exploited to coerce remote Windows servers, including Domain Controll...
Read More

IT Security News Weekly Summary – Week 29
IT Security News Daily Summary 2021-07-25 Threat actor offers Clubhouse secret database containing 3.8B phone numbers Robert M. Lee’s & ...
Read More
Fraud-as-a-Service – 2 Hackers Arrested by Dutch Cops for Sells & Rents Sophisticated Phishing Kits
Recently, the Dutch cops in the association of Group-IB have arrested two hackers for their testified association in a phishing fraud-as-a-s...
Read More

Cybersecurity Professionals to Newcomers: Focus on Vendor-Neutral Certifications
This article has been indexed from Cybersecurity Insiders Cybersecurity professionals are far more likely to hold vendor-specific certificat...
Read More
Top MITRE CWE 25 Most Dangerous Software Vulnerabilities – 2021
The American not-for-profit organization MITRE has recently published a list of CWE 25 of the most dangerous software vulnerabilities., The ...
Read More
Beware Of Fake Windows 11 Downloader that Installs Malware On Your Computer
Microsoft’s new Operating System, Windows 11 is officially set to be released this year. Before the official release, the Scammers are distr...
Read More

Girl Scouts Safeguards Data with BlackFog
This article has been indexed from Security Boulevard Girl Scouts North Carolina Coastal Pines serves 35,000+ girls and volunteers in 41 cou...
Read More

Flashpoint collaborates with Cybermerc to enhance its threat intelligence solution
This article has been indexed from Help Net Security Flashpoint announces a partnership with the Australian threat intelligence services pro...
Read More
What is Cyber Resilience and How it Helps Organization to Recover from Cyber Attacks
Do you want to know about Cyber Resilience? Then here you will get your answer in detail. Well, this is an organisation’s ability which acce...
Read More

Kaseya Gets Universal Decryptor to Help REvil Ransomware Victims
Nearly three weeks after Florida-based software vendor Kaseya was hit by a widespread supply-chain ransomware attack, the company on Thursda...
Read More

GTT’s portal feature provides expanded visibility into network security and performance
This article has been indexed from Help Net Security GTT Communications has announced the addition of the Secure Co-Manage feature to its Et...
Read More
New Xloader Malware Attack macOS & Windows Systems to Steal Login Credentials
There is a strong belief that Mac computers were resistant to malicious software, but, this idea has now changed over time. As the recent ev...
Read More
What is Sandboxing, Benefits, and How it Works?
Sandboxing comes under the cybersecurity section, which creates an isolated environment within the network that mimics the end-user operatin...
Read More

Ping Identity adds its IAM solutions to the Department of Homeland Security CDM APL
This article has been indexed from Help Net Security Ping Identity announced two of its Identity and Access Management (IAM) solutions have ...
Read More

Malicious NPM Package Caught Stealing Users' Saved Passwords From Browsers
A software package available from the official NPM repository has been revealed to be actually a front for a tool that's designed to ste...
Read More

New Windows and Linux Flaws Give Attackers Highest System Privileges
Microsoft's Windows 10 and the upcoming Windows 11 versions have been found vulnerable to a new local privilege escalation vulnerability...
Read More

Bosch upgrades its Dicentis system server with new hardware from HP
This article has been indexed from Help Net Security The Dicentis system server from Bosch has become very popular since its launch in 2019,...
Read More

This New Malware Hides Itself Among Windows Defender Exclusions to Evade Detection
Cybersecurity researchers on Tuesday lifted the lid on a previously undocumented malware strain dubbed "MosaicLoader" that singles...
Read More
Massive Data Leak Exposed a Pegasus spyware Used to Hack Cellphones of Journalists Globally
Recently, in a serious investigation, several security experts from the Guardian and The Washington Post along with Amnesty International an...
Read More

What’s Next for REvil’s Victims?
This article has been indexed from Threatpost Podcast: Nothing, says a ransomware negotiator who has tips on staying out of the sad subset o...
Read More

Researchers Warn of Linux Cryptojacking Attackers Operating from Romania
A threat group likely based in Romania and active since at least 2020 has been behind an active cryptojacking campaign targeting Linux-based...
Read More
D-Link Critical Flaw Let Attackers Execute Arbitrary Code And Obtain Sensitive Information
Cisco Talos, the threat intelligence research team of Cisco has recently identified and uncovered several critical security flaws in the rou...
Read More

White House Pressures Facebook To Remove Misinformation Quicker
This article has been indexed from Facecrooks The post White House Pressures Facebook To Remove Misinformation Quicker appeared first on Fac...
Read More

Chinese government issues new vulnerability disclosure regulations
This article has been indexed from Security Affairs Cyberspace Administration of China (CAC) issued new vulnerability disclosure regulations...
Read More
Top 10 Best Free Penetration Testing Tools 2021
When we talk about the penetration Testing tools, we all know very well that the first thing that comes up to our mind is the threat. As we ...
Read More

IT Security News Daily Summary 2021-07-17
Threat Actors are Working Together. Defenders Should Collaborate Too! XKCD ‘Board Game Argument: Legacy’ BSides Vancouver 2021 – Eric Payne’...
Read More

CloudFlare CDNJS Bug Could Have Led to Widespread Supply-Chain Attacks
Web infrastructure and website security company Cloudflare last month fixed a critical vulnerability in its CDNJS library that's used by...
Read More
New Unpatched Windows Print Spooler Bug Let Hackers Exploit The Elevation of Privilege
Microsoft issued a new security warning about the unpatched Windows Print Spooler Elevation of privilege vulnerability that allows attackers...
Read More

Red Hat renews FIPS 140-2 security validation for Red Hat Enterprise Linux 8.2
This article has been indexed from Help Net Security Red Hat announced the renewal of the Federal Information Processing Standard 140-2 (FIP...
Read More

The Definitive RFP Templates for EDR/EPP and APT Protection
Advanced Persistent Threats groups were once considered a problem that concerns Fortune 100 companies only. However, the threat landscape of...
Read More

Update Your Chrome Browser to Patch New Zero‑Day Bug Exploited in the Wild
Google has pushed out a new security update to Chrome browser for Windows, Mac, and Linux with multiple fixes, including a zero-day that it ...
Read More

Verge.io partners with CloudFabrix to provide data center transformation for organizations
This article has been indexed from Help Net Security Verge.io announced that CloudFabrix has selected the Verge-OS platform to form the basi...
Read More

China's Cyberspies Targeting Southeast Asian Government Entities
A sweeping and "highly active campaign" that originally set its sights on Myanmar has broadened its focus to strike a number of ta...
Read More

Health officials rail against Pfizer’s push for COVID boosters—for many reasons
This article has been indexed from HITBSecNews – Keeping Knowledge Free for Over a Decade Health officials rail against Pfizer’s push for CO...
Read More

Automatice su rutina de TI con la función de flujo de trabajo de OpManager
This article has been indexed from Security Boulevard Realizar las tareas diarias de TI puede ser bastante exigente, no porque todas las tar...
Read More
Kaseya Releases Patch and Restores VSA Servers Following Ransomware Attack
Kaseya released some emergency updates on July 11, and these updates also fix the vulnerabilities that are present in the Virtual System Adm...
Read More
Subscribe to:
Comments (Atom)