Recently, Cisco Talos discovered that the Transparent Tribe APT group is engaged in an ongoing malicious campaign. APT hackers from Pakistan...
Read More

Eskimi – 1,197,620 breached accounts
In late 2020, the AdTech platform Eskimi suffered a data breach that exposed 26M records with 1.2M unique email addresses. The data included...
Read More

Build or Buy your own antivirus product
We can help you decide if you should build your own antivirus product or if you should license an OEM or whitelabel product If you are think...
Read More
Uniswap Sophisticated Attack – Over $8 million worth of Ethereum Stolen
As a result of a sophisticated phishing attack, UniSwap, one of the most popular decentralized cryptocurrency exchanges, lost a large amount...
Read More

North Korean Hackers Targeting Small and Midsize Businesses with H0lyGh0st Ransomware
An emerging threat cluster originating from North Korea has been linked to developing and using ransomware in cyberattacks targeting small b...
Read More

Cyemptive Technologies CEO Rob Pike Named “Cybersecurity CEO of the Year” by CEO Monthly Magazine
SNOHOMISH, Wash.–(BUSINESS WIRE)–Cyemptive Technologies, the only cybersecurity company that guarantees threat elimination, today announced ...
Read More

Chariton Valley Commits To Protecting All Customers From Growing Cybersecurity Threats With Calix ProtectIQ Home Network Security
SAN JOSE, Calif.–(BUSINESS WIRE)–Calix, Inc. (NYSE: CALX) announced today that Chariton Valley Telephone Corporation (Chariton Valley) expec...
Read More

Black Hat Announces Chris Krebs & Kim Zetter As Keynote Speakers for Black Hat USA 2022
SAN FRANCISCO–(BUSINESS WIRE)–Black Hat, the producer of the cybersecurity industry’s most established and in-depth security events, announc...
Read More

Authenticating legacy apps with a reverse proxy
This blog was written by an independent guest blogger. When we think of “authentication” for our applications, most of us think of user regi...
Read More

Pakistani Hackers Targeting Indian Students in Latest Malware Campaign
The advanced persistent threat (APT) group known as Transparent Tribe has been attributed to a new ongoing phishing campaign targeting stude...
Read More

ERI Achieves Top ‘Quality of Work’ Ranking in Compliance Standards’ 2022 ITAD Vendor Reputation Ratings Survey
NEW YORK–(BUSINESS WIRE)–ERI, the nation’s largest fully integrated IT and electronics asset disposition provider and cybersecurity-focused ...
Read More

New 'Retbleed' Speculative Execution Attack Affects AMD and Intel CPUs
Security researchers have uncovered yet another vulnerability affecting numerous older AMD and Intel microprocessors that could bypass curre...
Read More

🚀 Launching Autonomous SecOps (Your Virtual, Algorithm-Driven Tier 1 SOC Team)
We are helping security teams go beyond individual file analysis to automate their entire Endpoint and Email alert triage processes with our...
Read More
Cloud-Based Cryptocurrency Miners Abuse GitHub Actions & Azure to Mine Cryptocurrency
The GitHub Actions as well as the Azure VMs are constantly being targeted by threat actors for the purpose of mining cryptocurrency in the c...
Read More
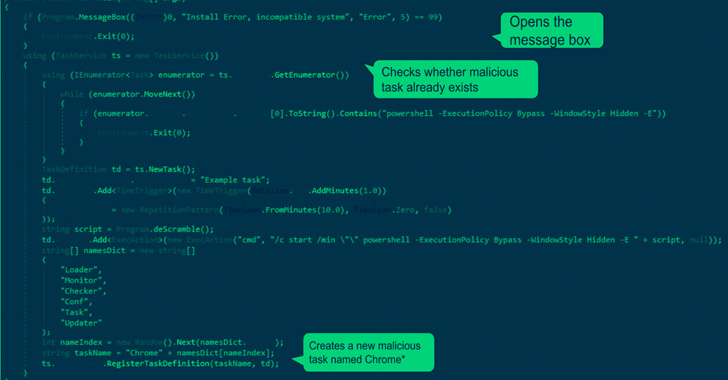
Researchers Uncover New Variants of the ChromeLoader Browser Hijacking Malware
Cybersecurity researchers have uncovered new variants of the ChromeLoader information-stealing malware, highlighting its evolving feature se...
Read More
Microsoft Releases Fix for Zero-Day Flaw in July 2022 Security Patch Rollout
Microsoft released its monthly round of Patch Tuesday updates to address 84 new security flaws spanning multiple product categories, countin...
Read More

Check Point Software Technologies announces the integration of CloudGuard Network Security with AWS Cloud WAN Service
By Jeff Engel, Cloud Security Technical Marketing Engineer, published July 12, 2022 Background As more and more organizations transition wor...
Read More

Severe Remote Code Execution Vulnerability Riddled OpenSSL
The recent OpenSSL updates address two security bugs in the service, including a high-severity vulnerability… Severe Remote Code Execution V...
Read More
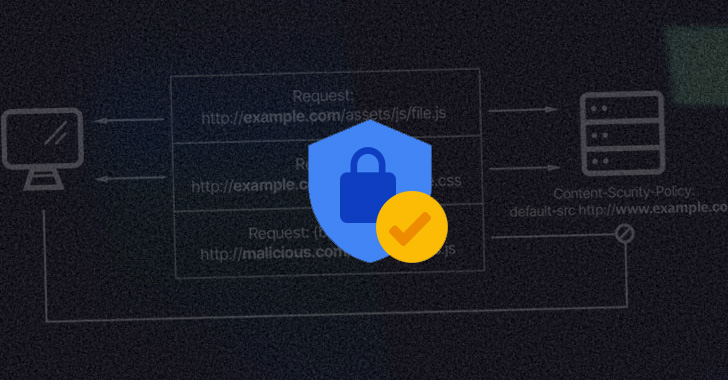
Avoiding Death by a Thousand Scripts: Using Automated Content Security Policies
Businesses know they need to secure their client-side scripts. Content security policies (CSPs) are a great way to do that. But CSPs are cum...
Read More
OrBit – Undetected Linux Malware Uses Unseen Hijack Method to Attack Linux Systems
Servers and cloud computing infrastructures are commonly powered by Linux, a popular operating system. And recently a new and completely und...
Read More
Rozena Backdoor Malware Uses a Fileless Attack to Injecting Remote shell on Windows
In order to distribute a previously undocumented backdoor named Rozena on Windows systems, an phishing campaign has recently been observed t...
Read More

HavanaCrypt ransomware sails in as a fake Google update
Difficult to detect, hiding its window by using the ShowWindow function in Windows A new ransomware family is being delivered as a bogus Goo...
Read More

Associated Eye Care Discloses Impact From 2020 Netgain Ransomware Attack
Montana-based Associated Eye Care Partners (AEC) has started informing patients that their personal data might have been compromised during ...
Read More
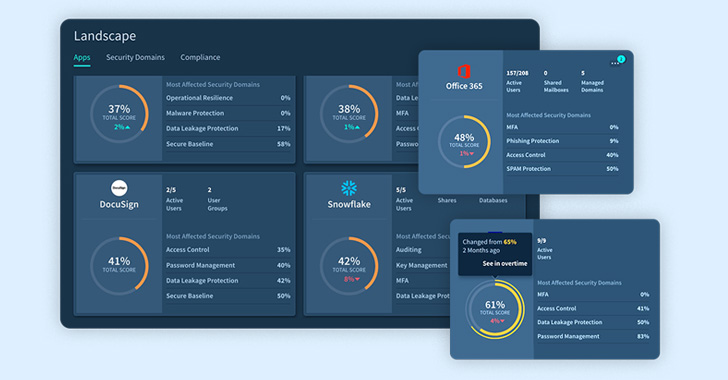
What It Takes to Tackle Your SaaS Security
It's not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc., are amazing for enabling the hybrid workforce...
Read More

✨ Happy Birthday to EFF!
Today at the Electronic Frontier Foundation, we’re celebrating 32 years of fighting for technology users around the world. If you were onlin...
Read More

PyPI Repository Makes 2FA Security Mandatory for Critical Python Projects
The maintainers of the official third-party software repository for Python have begun imposing a new two-factor authentication (2FA) conditi...
Read More

Iraq in the Era of the Abraham Accords
President Biden meets with Prime Minister Mustafa al-Kadhimi of Iraq at the White House on July 26, 2021. Photo credit: Official White House...
Read More

OISF 2022
OISF 2022These are the videos from the OISF Anniversary Event. Intro Becoming an IR SuperstarMatt Scheurer Ransomware Is NOT the problemScot...
Read More

Musk Ditches Twitter Deal, Triggering Defiant Response
Elon Musk on Friday pulled the plug on his $44 billion deal to buy Twitter, accusing the social media giant of “misleading” statements about...
Read More

Week in review: Quantum-resistant encryption, attackers using deepfakes, Patch Tuesday forecast
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Healthcare organizations targeted with Mau...
Read More

ID.me appoints David Kensick as Chief Experience Officer
ID.me announced the appointment of David Kensick as Chief Experience Officer. In his new role, Kensick will focus on continuing to improve t...
Read More

A Complete Guide to Perform External Penetration Testing on Your Client Network | Step-by-Step Methods
This write-up walks us through one of my many journeys in my external penetration testing and how I compromised the organization in this wri...
Read More
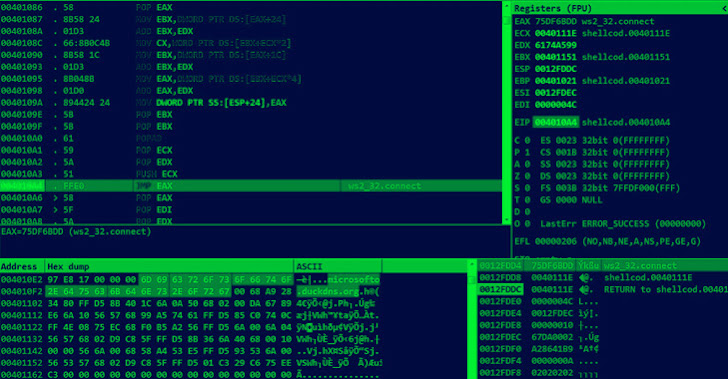
Hackers Exploiting Follina Bug to Deploy Rozena Backdoor
A newly observed phishing campaign is leveraging the recently disclosed Follina security vulnerability to distribute a previously undocument...
Read More

Driving to France this summer? Watch out for scam websites before you go
Scammers don’t take the summer off – be on your guard when buying your Crit’Air sticker The post Driving to France this summer? Watch out fo...
Read More

Avoid travel digital disasters – Week in security with Tony Anscombe
Vacations are a great time to unwind, but if you’re not careful, you may face a digital disaster. Here’s how to keep your devices and data s...
Read More

Why Developers Hate Changing Language Versions
Progress powers technology forward. But progress also has a cost: by adding new capabilities and features, the developer community is consta...
Read More

Apple Announce New “Lockdown Mode” Security Feature to Protect Journalists
Apple has announced a new set of features for iPhone called “Lockdown Mode.” On Wednesday, the tech giant wrote in a blog post that Lockdown...
Read More
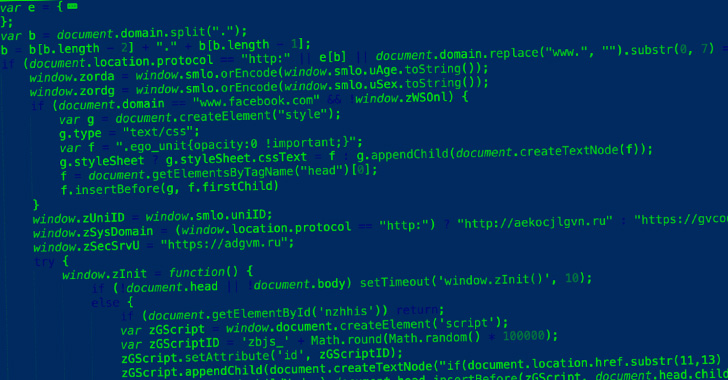
Experts Uncover 350 Browser Extension Variants Used in ABCsoup Adware Campaign
A malicious browser extension with 350 variants is masquerading as a Google Translate add-on as part of an adware campaign targeting Russian...
Read More

T Mobile Business confirms data breach again
T Mobile’s Executive Vice President Mike Katz issued an update on his LinkedIn page, a sophisticated cyber attack resulting in data breach t...
Read More

Cisco and Fortinet Release Security Patches for Multiple Products
Cisco on Wednesday rolled out patches for 10 security flaws spanning multiple products, one of which is rated Critical in severity and could...
Read More
Apple New Lockdown Mode to Protect Users from Highly Targeted Cyberattacks
Apple introduced ‘Lockdown’ mode, a security setting that gives specialized additional protection to users who may be at risk of highly targ...
Read More

Do you know what your supply chain is and if it is secure?
The recent attacks on the software supply chains of big software producers showed us that this component has not received the needed attenti...
Read More

Heimdal™ Successfully Completes SOC 2 Type II and ISAE 3000 Examination, Indicating Strict Security Standards Compliance
COPENHAGEN, July 6th, 2022 – Heimdal™ is pleased to announce it has attained certification for ISAE 3000 SOC 2 Type II, demonstrating a comm...
Read More

For the Love of the Wild Web 🖤
There is a traditional Japanese concept called wabi-sabi that recognizes the world as impermanent, evolving, and unfinished. You could call ...
Read More

Researchers Warn of New OrBit Linux Malware That Hijacks Execution Flow
Cybersecurity researchers have taken the wraps off a new and entirely undetected Linux threat dubbed OrBit, signally a growing trend of malw...
Read More
Threat Actors Claimed that They Have Stolen Data of a Billion Chinese Residents
A hacker claimed to have stolen one billion Chinese residents’ records from the Shanghai National Police database, which is considered the l...
Read More

As New Clues Emerges, Experts Wonder: Is REvil Back?
Change is a part of life, and nothing stays the same for too long, even with hacking groups, which are at their most dangerous when working ...
Read More
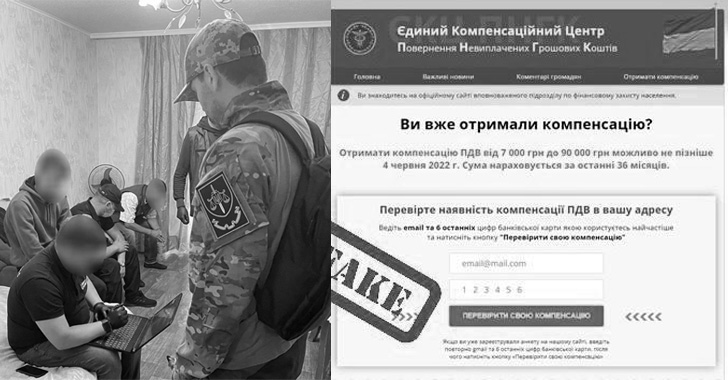
Ukrainian Authorities Arrested Phishing Gang That Stole 100 Million UAH
The Cyber Police of Ukraine last week disclosed that it apprehended nine members of a criminal gang that embezzled 100 million hryvnias via ...
Read More

Some Worms Use Their Powers for Good
Gardeners know that worms are good. Cybersecurity professionals know that worms are bad. Very bad. In fact, worms are literally the most dev...
Read More

HackerOne Employee Caught Stealing Vulnerability Reports for Personal Gains
Vulnerability coordination and bug bounty platform HackerOne on Friday disclosed that a former employee at the firm improperly accessed secu...
Read More
Subscribe to:
Comments (Atom)