Microsoft said that Nobelium, a Russian-based hacking group, launched the phishing campaign by gaining access to a marketing account of the ...
Read More
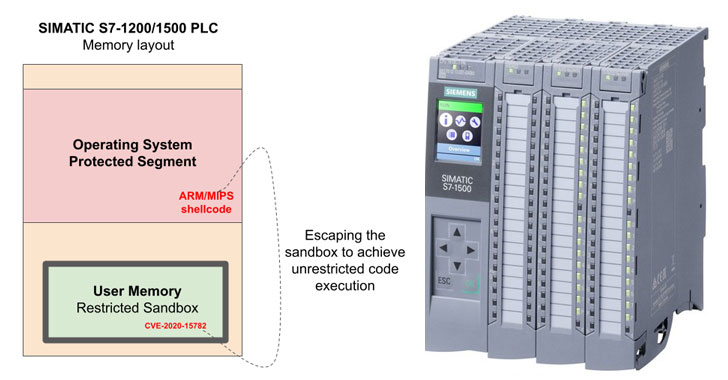
A New Bug in Siemens PLCs Could Let Hackers Run Malicious Code Remotely
Siemens on Friday shipped firmware updates to address a severe vulnerability in SIMATIC S7-1200 and S7-1500 programmable logic controllers (...
Read More

BSides Canberra 2021 – Sean Yeoh’s, Patrick Mortensen’s, Michael Gianarakis’ And Shubham Shah’s ‘Context Aware Content Discovery: The Natural Evolution’
This article has been indexed from Security Boulevard Thanks to BSides Canberra for publishing their outstanding videos on the organization’...
Read More

Apple’s M1 Chip Has a Fascinating Flaw
This article has been indexed from Security Latest The covert channel bug demonstrates a fundamental fact of CPUs: even new ones have vulner...
Read More
Growing Log Management Platform Logit.io Launches Dedicated UK Data Centre
Leading log management and metrics company Logit.io is pleased to announce that they have expanded their offering to include a new dedicated...
Read More

US Soldiers Exposed Nuclear Secrets on Digital Flash Ccards
This article has been indexed from Security Latest Plus: A major hack in Japan, Citizen app run amok, and more of the week’s top security ne...
Read More

SonicWall Urges Customers to ‘immediately’ Patch NSM On-Prem Bug
This article has been indexed from E Hacking News – Latest Hacker News and IT Security News SonicWall urges customers to “immediately” pat...
Read More

Researchers Demonstrate 2 New Hacks to Modify Certified PDF Documents
Cybersecurity researchers have disclosed two new attack techniques on certified PDF documents that could potentially enable an attacker to a...
Read More
The Various Ways in Which Someone Can Remotely Monitor Your Android Device
Monitor Your Android Device Technology today is so advanced that one always needs to be careful about the kind of information they share and...
Read More

Chinese Cyber Espionage Hackers Continue to Target Pulse Secure VPN Devices
Cybersecurity researchers from FireEye unmasked additional tactics, techniques, and procedures (TTPs) adopted by Chinese threat actors who w...
Read More

SolarWinds Hackers Target Think Tanks With New 'NativeZone' Backdoor
Microsoft on Thursday disclosed that the threat actor behind the SolarWinds supply chain hack returned to the threat landscape to target gov...
Read More

Identity, credentials and behavior are critical to network protection
This article has been indexed from GCN: News, Explainers, Insights In a post-pandemic economy with employees outside the firewall, agencies ...
Read More
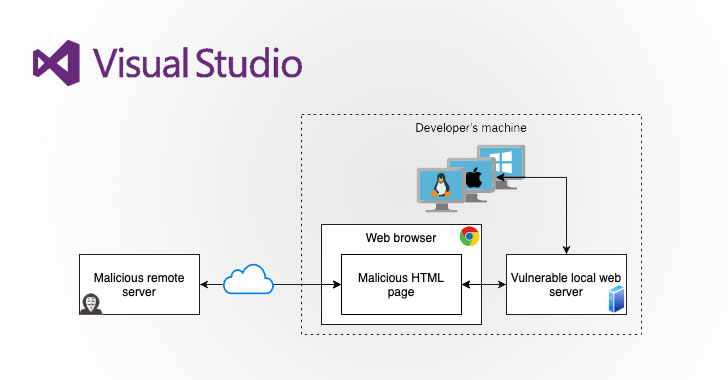
Newly Discovered Bugs in VSCode Extensions Could Lead to Supply Chain Attacks
Severe security flaws uncovered in popular Visual Studio Code extensions could enable attackers to compromise local machines as well as buil...
Read More

Hackers Using Fake Foundations to Target Uyghur Minority in China
The Uyghur community located in China and Pakistan has been the subject of an ongoing espionage campaign aiming to trick the targets into do...
Read More

How user experience is shaping verifiable credentials and identity
This article has been indexed from Microsoft Security Since 2017, Microsoft has been working with the identity community on two groundbreaki...
Read More
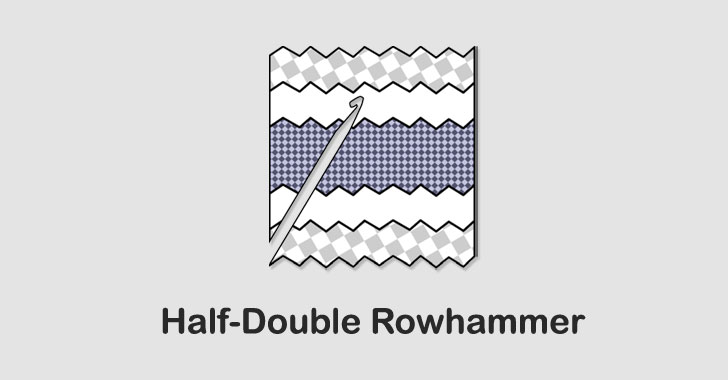
Google Researchers Discover A New Variant of Rowhammer Attack
A team of security researchers from Google has demonstrated yet another variant of the Rowhammer attack that bypasses all current defenses t...
Read More

Critical RCE Vulnerability Found in VMware vCenter Server — Patch Now!
VMware has rolled out patches to address a critical security vulnerability in vCenter Server that could be leveraged by an adversary to exec...
Read More

Who are you? Rising to the data protection challenge
This article has been indexed from GCN: News, Explainers, Insights Mainframes allow agencies to implement zero trust, multifactor authentica...
Read More

New Bluetooth Flaws Let Attackers Impersonate Legitimate Devices
Adversaries could exploit newly discovered security weaknesses in Bluetooth Core and Mesh Profile Specifications to masquerade as legitimate...
Read More

Apple Issues Patches to Combat Ongoing 0-Day Attacks on macOS, tvOS
Apple on Monday rolled out security updates for iOS, macOS, tvOS, watchOS, and Safari web browser to fix multiple vulnerabilities, including...
Read More
Top 10 Vulnerability Assessment and Penetration Testing (VAPT) Tools
VAPT Tools are playing the most important part in penetration testing, Here we have listed to top 10 most used VAPT tools for both free and ...
Read More

What To Do When Your Business Is Hacked
As businesses move to a remote workforce, hackers have increased their activity to capitalize on new security holes. Cybercriminals often us...
Read More
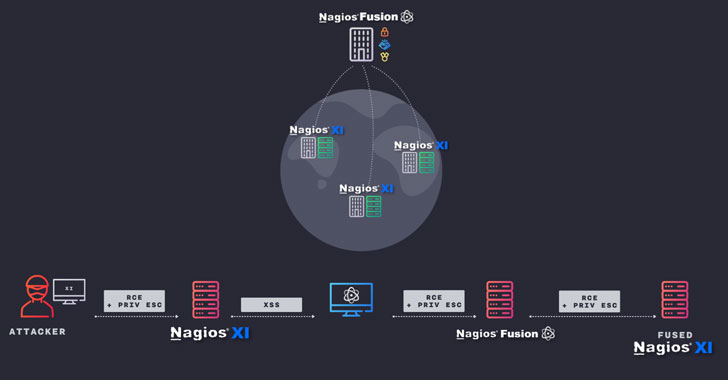
Details Disclosed On Critical Flaws Affecting Nagios IT Monitoring Software
Cybersecurity researchers disclosed details about 13 vulnerabilities in the Nagios network monitoring application that could be abused by an...
Read More

CPDP 2021 – Moderator: Seda Gürses ‘Connecting The Dots: Privacy, Data, Racial Justice’
This article has been indexed from Security Boulevard Speakers: Yasmine Boudiaf, Sarah Chander, Nakeema Stefflbauer, Nani Jansen Reventlow, ...
Read More

Security Affairs newsletter Round 315
This article has been indexed from Security Affairs A new round of the weekly SecurityAffairs newsletter arrived! Every week the best securi...
Read More

India’s National Carrier Says Hack Leaked Passengers’ Data
This article has been indexed from SecurityWeek RSS Feed Personal data of an unspecified number of travelers has been compromised after a co...
Read More

Foreign hackers breached Russian federal agencies, said FSB
This article has been indexed from Security Affairs FSB National Coordination Center for Computer Incidents (NKTsKI) revealed that foreign h...
Read More

FBI Warns Conti Ransomware Hit 16 U.S. Health and Emergency Services
The adversary behind Conti ransomware targeted no fewer than 16 healthcare and first responder networks in the U.S. within the past year, to...
Read More

Air India Hack Exposes Credit Card and Passport Info of 4.5 Million Passengers
India's flag carrier airline, Air India, has disclosed a data breach affecting 4.5 million of its customers over a period stretching nea...
Read More
10 Best Free Web Application Penetration Testing Tools 2021
Web Application Pentesting Tools are the most essential part of the penetration testing process when it comes to web-based applications. We ...
Read More

Insurance Firm CNA Financial Reportedly Paid Hackers $40 Million in Ransom
U.S. insurance giant CNA Financial reportedly paid $40 million to a ransomware gang to recover access to its systems following an attack in ...
Read More

Microsoft Warns of Data Stealing Malware That Pretends to Be Ransomware
Microsoft on Thursday warned of a "massive email campaign" that's pushing a Java-based STRRAT malware to steal confidential da...
Read More
Over 150 Flaws in 58 Stalkerware Apps Let Attackers Steal Control and Carry out Malicious Activities
Spouseware. Nope! Not the term used when your spouse troubles you! It is a mobile monitoring software, also known as mobile stalkerware. Thi...
Read More

Watering Hole Attack Was Used to Target Florida Water Utilities
An investigation undertaken in the aftermath of the Oldsmar water plant hack earlier this year has revealed that an infrastructure contracto...
Read More

Android Issues Patches for 4 New Zero-Day Bugs Exploited in the Wild
Google on Wednesday updated its May 2021 Android Security Bulletin to disclose that four of the security vulnerabilities that were patched e...
Read More
A New Unique RAT Heavily Uses The Autohotkey Scripting Language On An Ongoing Malware Campaign
The Morphisec Labs team has tracked a unique and ongoing RAT delivery campaign that heavily uses the AutoHotKey scripting language, a fork o...
Read More
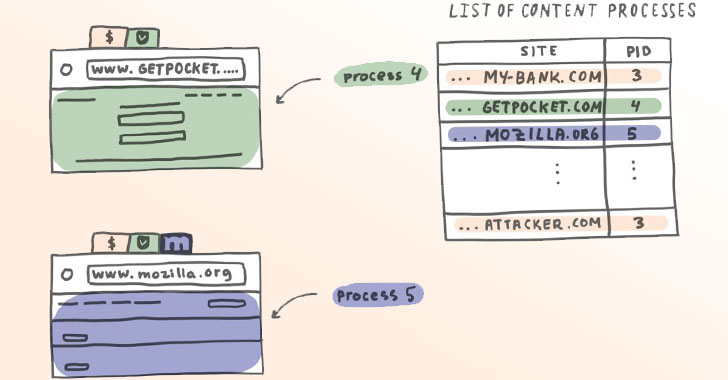
Mozilla Begins Rolling Out 'Site Isolation' Security Feature to Firefox Browser
Mozilla has begun rolling out a new security feature for its Firefox browser in nightly and beta channels that aims to protect users against...
Read More
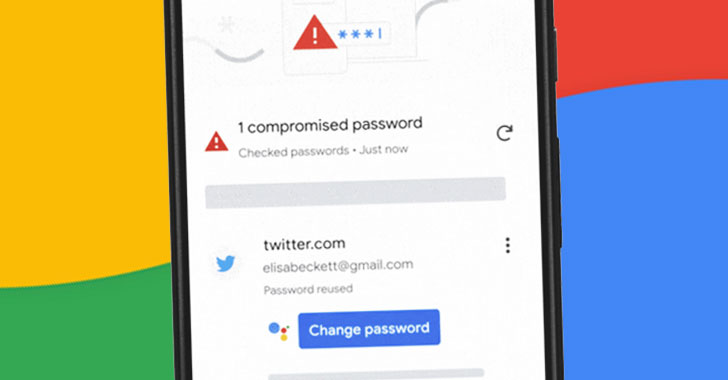
A Simple 1-Click Compromised Password Reset Feature Coming to Chrome Browser
Google on Tuesday announced a new feature to its password manager that could be used to change a stolen password automatically with a single...
Read More
Apple Rejected more than 350000 Apps in 2020 that Contains Malicious Features
Apple disclosed that it rejected more than 350000 malicious apps from its App Store in 2020 and stopped more than $1.5billion in potentially...
Read More

Experts Reveal Over 150 Ways to Steal Control of 58 Android Stalkerware Apps
A total of 158 privacy and security issues have been identified in 58 Android stalkware apps from various vendors that could enable a malici...
Read More

70 European and South American Banks Under Attack By Bizarro Banking Malware
A financially motivated cybercrime gang has unleashed a previously undocumented banking trojan, which can steal credentials from customers o...
Read More
Hackers Abuse Microsoft Build Engine to Deliver Password-Stealing Malware Filelessly
Anomali Threat Research recognized a campaign in which threat actors used Microsoft Build Engine (MSBuild) to filelessly deliver Remcos remo...
Read More

Why Password Hygiene Needs a Reboot
In today's digital world, password security is more important than ever. While biometrics, one-time passwords (OTP), and other emerging ...
Read More

Experts Warn About Ongoing AutoHotkey-Based Malware Attacks
Cybersecurity researchers have uncovered an ongoing malware campaign that heavily relies on AutoHotkey (AHK) scripting language to deliver m...
Read More

Remote Mouse App Crippled With ‘Mouse Trap’ Zero-Day Bugs
This article has been indexed from Latest Hacking News Remote Mouse mobile app has some serious security flaws that it hasn’t addressed yet....
Read More
What is Command and Control(C2) Server – A Detailed Overview
Like a regular system holder, you might be wondering why is your system running slower than usual? Always you are getting random messages li...
Read More
Popular Russian Hacking Forum XSS Bans all the Topics Promoting Ransomware
XSS, the Russian-speaking hacker forums have banned all topics publicizing ransomware to prevent unwanted attention and to share knowledge a...
Read More

‘Build’ or ‘Buy’ your own antivirus product
We can help you decide if you should build your own antivirus product or if you should license an OEM or whitelabel product Both options com...
Read More

Cisco has Fixed a six-month-Old Zero-day Vulnerability Found in the Cisco AnyConnect
This article has been indexed from GBHackers On Security The Cisco Product Security Incident Response Team (PSIRT) has recently fixed a six-...
Read More
Rapid7 has Disclosed that Some Code Repositories were Accessed in Codecov Supply-Chain Attack
Cybersecurity vendor Rapid7 disclosed it was among the victims of the Codecov software supply chain attack and warned that data for a subset...
Read More
Subscribe to:
Comments (Atom)